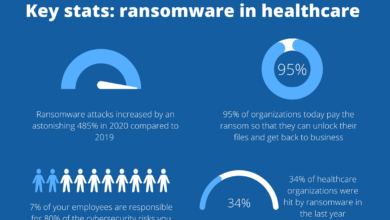
Ascension Cyberattack EHR, Pharmacy, Ambulance Impact
Ascension cyberattack impact ehr pharmacy ambulance diversion – that’s a mouthful, isn’t it? But it perfectly captures the cascading chaos unleashed when a healthcare giant like Ascension falls victim to a major cyberattack. This wasn’t just a data breach; it crippled essential services, from accessing patient records to dispatching ambulances. We’re diving deep into the fallout, exploring the vulnerabilities exposed, the ripple effects felt across different healthcare sectors, and what we can learn to prevent future disasters.
This post will examine the specific ways this attack affected Electronic Health Records (EHRs), pharmacy operations, and ambulance services. We’ll look at the interconnectedness of these systems and how a breach in one area can trigger a domino effect across the entire healthcare network. We’ll also discuss the legal and ethical implications of such a massive data breach, and explore strategies for improving cybersecurity resilience within the healthcare industry.
Impact on Electronic Health Records (EHR) Systems: Ascension Cyberattack Impact Ehr Pharmacy Ambulance Diversion

Source: zerosecurity.org
The Ascension cyberattack highlighted the significant vulnerabilities present within even the most sophisticated healthcare electronic health record (EHR) systems. These systems, while designed to improve patient care and streamline administrative tasks, are complex networks containing vast amounts of sensitive patient data, making them prime targets for malicious actors. A successful breach can have far-reaching and devastating consequences for both patients and the healthcare provider.The potential vulnerabilities exploited during such an attack could include outdated software, weak passwords, insufficient network security, and a lack of robust access controls.
Attackers might leverage phishing emails to gain initial access, exploit known software vulnerabilities, or employ more sophisticated techniques like ransomware to encrypt critical data and demand a ransom for its release. The specific vulnerabilities exploited in the Ascension attack remain partially undisclosed, but the incident serves as a stark reminder of the ever-evolving nature of cyber threats and the need for continuous vigilance.
Data Breaches and Their Consequences
Data breaches in EHR systems resulting from cyberattacks like the one targeting Ascension can compromise a wide range of sensitive patient information, including protected health information (PHI) such as medical history, diagnoses, treatment plans, insurance details, and even financial information. This exposure violates patient privacy, potentially leading to identity theft, medical fraud, and emotional distress. Beyond the patient level, operational disruptions can be significant.
Healthcare operations can be severely hampered, delaying or preventing access to critical patient data, impacting treatment decisions, and causing delays in billing and other administrative processes. The ripple effects can extend to insurance providers, regulatory bodies, and the public’s trust in the healthcare system itself. For example, a delay in accessing patient allergies could lead to a medication error, highlighting the real-world impact of such breaches.
EHR System Recovery and Restoration
Recovering and restoring EHR systems after a successful cyberattack is a complex and multifaceted process. It typically involves several crucial steps. First, containing the breach is paramount, isolating affected systems to prevent further damage and data exfiltration. Next, a thorough forensic investigation is necessary to identify the extent of the breach, the methods used by the attackers, and the specific data compromised.
This is followed by the restoration of affected systems from backups, ensuring data integrity and system functionality. Finally, robust security measures must be implemented to prevent future attacks, including patching vulnerabilities, strengthening access controls, and implementing multi-factor authentication. The entire process can be lengthy and resource-intensive, requiring the expertise of cybersecurity professionals, IT specialists, and legal counsel.
Financial and Reputational Costs of EHR Breaches
The financial and reputational costs associated with EHR system breaches can be substantial and long-lasting.
| Cost Type | Potential Costs | Example | Impact |
|---|---|---|---|
| Financial | Incident response costs, legal fees, regulatory fines, remediation expenses, loss of revenue, ransom payments | A large healthcare system might spend millions on incident response, legal fees, and system restoration. | Significant financial burden, potentially impacting profitability and future investments. |
| Reputational | Loss of patient trust, damage to brand image, decreased market share, difficulty attracting and retaining staff | Negative media coverage can lead to a decline in patient volume and a negative impact on employee morale. | Long-term impact on the organization’s standing and ability to operate effectively. |
| Legal | Lawsuits from patients, regulatory investigations, potential criminal charges | Class-action lawsuits can result in massive payouts and ongoing legal battles. | Significant financial and operational disruption, potentially leading to bankruptcy. |
| Operational | Disruption of healthcare services, delays in patient care, loss of productivity | Inability to access patient records can lead to treatment delays and medical errors. | Direct impact on patient safety and the quality of care provided. |
Disruption of Pharmacy Operations
The Ascension cyberattack, like any large-scale breach, had the potential to severely disrupt pharmacy operations, impacting everything from prescription fulfillment to patient safety. The reliance on electronic systems for prescription management, inventory control, and patient record access makes pharmacies particularly vulnerable to such attacks. A successful breach could lead to significant operational challenges and potentially compromise patient data.The consequences of a cyberattack on pharmacy systems are multifaceted and far-reaching.
Disruption of prescription drug dispensing could lead to delays in patients receiving necessary medications, potentially resulting in adverse health outcomes. Inventory management systems, often integrated with EHRs, could be compromised, leading to inaccurate stock levels and difficulties in ordering and restocking medications. This could cause shortages of essential drugs, further impacting patient care. The loss or compromise of patient data, including personal information and prescription histories, could have serious legal and ethical implications.
Challenges in Maintaining Patient Care Continuity During System Outages
Maintaining patient care continuity during a system outage presents significant challenges for pharmacies. Pharmacies rely heavily on electronic systems for accurate and efficient dispensing of medications. Without these systems, pharmacists may struggle to verify prescriptions, access patient medication histories, or manage inventory effectively. This can lead to medication errors, delays in dispensing, and patient frustration. The inability to access electronic records could also impact communication with other healthcare providers, potentially hindering coordinated patient care.
In the case of a widespread outage, the lack of access to critical information could create significant challenges for emergency services and patient safety.
Mitigation Strategies for Pharmacies
Pharmacies can implement various strategies to mitigate the impact of cyberattacks. These strategies should focus on preventing attacks, detecting breaches quickly, and having robust recovery plans in place. A crucial aspect is investing in robust cybersecurity infrastructure, including firewalls, intrusion detection systems, and regular security audits. Employee training on cybersecurity best practices is also vital to prevent phishing attacks and other social engineering tactics.
Maintaining offline backups of critical data is essential to ensure business continuity during an outage. Furthermore, pharmacies should develop and regularly test incident response plans to ensure they can quickly recover from an attack. Regularly updating software and operating systems is also crucial to patch security vulnerabilities. Finally, having clear communication protocols in place to inform patients and healthcare providers about service disruptions is vital to maintaining trust and patient safety.
Implementing Robust Cybersecurity Measures: A Step-by-Step Procedure
Implementing robust cybersecurity measures requires a systematic and proactive approach. The following steps Artikel a procedure for pharmacies to enhance their security posture:
1. Conduct a Risk Assessment
Identify vulnerabilities in the pharmacy’s IT infrastructure and systems.
2. Develop a Cybersecurity Policy
The Ascension cyberattack’s impact on EHRs, pharmacies, and ambulance diversion is a serious issue, highlighting our vulnerability to digital threats. It makes you wonder about the resilience of our healthcare system, especially considering how reliant we are on technology. The news that the FDA approves clinical trials for pig kidney transplants in humans is fascinating, but it also underscores how much we need robust systems to manage such advancements, systems that are protected from attacks like the one on Ascension.
Without secure data, even groundbreaking medical progress could be severely hampered.
Create a comprehensive policy outlining security protocols and responsibilities.
3. Implement Strong Access Controls
Use strong passwords, multi-factor authentication, and role-based access control.
The Ascension cyberattack’s impact on EHR systems caused widespread pharmacy disruptions and ambulance diversions, really stressing healthcare workers. The constant clicking and typing to workaround the system issues left many of us with painful wrists, so I started researching ways to manage the pain; I found some helpful advice on ways to treat carpal tunnel syndrome without surgery , which has been a lifesaver.
Hopefully, things will improve soon, but until then, I’m focusing on self-care to manage the fallout from this massive cyberattack.
4. Install and Maintain Security Software
Regularly update antivirus, anti-malware, and firewall software.
5. Educate Employees
Provide regular training on cybersecurity best practices, including phishing awareness.
6. Regularly Back Up Data
Implement a robust backup and recovery plan to protect against data loss.
7. Monitor Systems
Regularly monitor systems for suspicious activity and promptly address any security incidents.
8. Conduct Regular Security Audits
Conduct periodic security audits to identify and address vulnerabilities.
9. Develop an Incident Response Plan
Create a detailed plan outlining steps to take in the event of a security breach.1
0. Stay Updated
Keep abreast of the latest cybersecurity threats and best practices.
Effects on Ambulance Services and Patient Diversion
The Ascension cyberattack, impacting numerous healthcare systems, had significant ripple effects far beyond the immediate disruption of EHRs and pharmacies. A crucial area affected was emergency medical services (EMS), specifically ambulance dispatch and patient transport. The attack’s reach into communication networks and operational systems created a cascade of problems impacting patient care and resource allocation.The disruption to ambulance dispatch and routing systems stemmed from the attack’s potential compromise of crucial communication infrastructure.
Many ambulance services rely on computerized dispatch systems linked to hospitals and other healthcare facilities. If these systems were compromised, as was potentially the case with the Ascension attack, dispatchers may have experienced difficulties in receiving calls, locating ambulances, or providing accurate routing information to emergency responders. This compromised communication infrastructure directly affected the ability of EMS to respond efficiently and effectively.
Compromised Communication Systems and Emergency Response Times
Compromised communication systems directly translate to delays in emergency response times. Ambulance crews might have been unable to receive crucial patient information, leading to delayed or improperly equipped responses. Dispatchers may have faced difficulties contacting hospitals to confirm bed availability, leading to ambulances being diverted unnecessarily, causing further strain on resources. In the chaotic aftermath of a large-scale cyberattack, the inability to rapidly communicate effectively between dispatchers, paramedics, and hospitals can lead to significantly worse patient outcomes, including increased mortality rates in time-sensitive situations such as heart attacks or strokes.
Consider a scenario where an ambulance crew, unable to contact the hospital, is forced to spend valuable time searching for an alternative facility, delaying critical care for a stroke victim.
Impact of Ambulance Diversion Strategies
The Ascension cyberattack’s impact on hospital systems directly affected ambulance diversion strategies. Ambulance diversion, a tactic used when a hospital’s emergency department is overwhelmed, involves redirecting ambulances to alternative facilities. If the attack compromised hospital systems tracking bed availability or patient status, dispatchers may have lacked real-time information, leading to inefficient diversion decisions. This could result in ambulances being sent to already overloaded hospitals or to facilities farther away, increasing transport times and exacerbating delays in patient care.
This increased strain on the healthcare system, particularly during peak demand periods, could potentially lead to a surge in preventable deaths and longer waiting times for non-emergency patients as well.
Strategies for Improving Ambulance Service Resilience to Cyberattacks
Improving the resilience of ambulance services to cyberattacks requires a multi-faceted approach. It is crucial to implement robust cybersecurity measures and establish effective incident response plans.
- Invest in robust cybersecurity infrastructure: This includes employing advanced firewalls, intrusion detection systems, and regular security audits to identify and mitigate vulnerabilities.
- Implement redundant communication systems: Diversifying communication channels, such as using backup radio systems or satellite communication, ensures continued operational capability even if primary systems are compromised.
- Develop comprehensive incident response plans: These plans should Artikel procedures for responding to cyberattacks, including communication protocols, data backup and recovery strategies, and coordination with other emergency services.
- Regular cybersecurity training for staff: Educating dispatchers and paramedics about phishing scams, malware, and other cyber threats can significantly reduce the risk of human error.
- Establish strong partnerships with hospitals and healthcare providers: Collaborative efforts in cybersecurity preparedness and incident response can improve overall resilience across the healthcare ecosystem.
Interconnectedness of Healthcare Systems
The recent Ascension cyberattack highlighted a terrifying reality: our healthcare systems are deeply interconnected, and a breach in one area can rapidly cascade into others, causing widespread disruption and patient harm. Understanding the vulnerabilities within each system and how they interact is crucial for building more resilient infrastructure.The vulnerabilities of EHRs, pharmacies, and ambulance services differ significantly, yet they are all interconnected in ways that amplify the impact of a cyberattack.
EHR systems, often the central hub of patient data, are vulnerable to data breaches exposing sensitive medical information. Pharmacies, reliant on electronic prescriptions and inventory management systems, face disruptions to medication dispensing and supply chains. Ambulance services, depending on real-time communication and location tracking, are susceptible to delays and misdirection.
Vulnerability Comparisons of Healthcare Systems
EHR systems are attractive targets due to the wealth of sensitive patient data they hold. A successful attack could lead to data theft, ransomware encryption locking access to patient records, and disruption of clinical workflows. Pharmacies, while less data-rich than EHRs, are vulnerable to supply chain disruptions through compromised inventory systems, leading to medication shortages. Ambulance services, dependent on communication networks and GPS systems, are susceptible to operational paralysis if their systems are compromised, leading to delayed responses and potential patient harm.
The reliance on interconnected systems magnifies these individual vulnerabilities.
Cascading Effects of a Cyberattack
A successful attack on one system can trigger a domino effect. For example, a ransomware attack on an EHR system could prevent ambulance crews from accessing critical patient information, delaying treatment. Simultaneously, a compromised pharmacy system might hinder the timely dispensing of necessary medications, further complicating patient care. The disruption extends beyond immediate effects, impacting long-term care planning and potentially leading to increased hospital readmissions.
The interconnected nature of these systems ensures that even a seemingly isolated attack on one system can have broad consequences.
Hypothetical Scenario: A Large-Scale Breach
Imagine a scenario where a sophisticated cyberattack targets a major hospital’s EHR system. The attackers encrypt patient data and demand a ransom. Simultaneously, they disrupt the pharmacy’s inventory management system, leading to medication shortages. Ambulance services, relying on the EHR for patient information, experience delays as they struggle to access vital details. This results in delayed responses, longer hospital wait times, and potentially, preventable patient deaths.
The cascading effect is a complete collapse of healthcare services within a region.
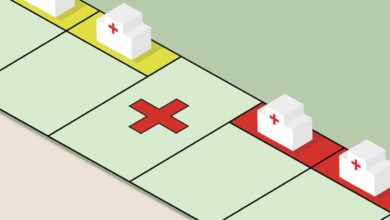
Illustration of Information Flow and Attack Impact
Imagine a diagram showing three interconnected circles representing the EHR, pharmacy, and ambulance systems. Arrows illustrate the flow of information: prescriptions from EHR to pharmacy, patient location data from ambulance to EHR, and medication details from pharmacy to ambulance. A large red X marks the EHR system, indicating the point of attack. From this point, red lines extend to the pharmacy and ambulance systems, showing how the disruption spreads, affecting the flow of information and creating bottlenecks at every point of connection.
The overall effect is a severely crippled healthcare network, unable to function efficiently or safely. The diagram visually demonstrates how a single point of failure can cripple the entire system.
The Ascension cyberattack’s impact on EHR systems caused widespread disruption, affecting pharmacies and even leading to ambulance diversions. It’s a stark reminder of how vulnerable our systems are, and it made me think about how we manage vulnerabilities in other areas of life, like the challenges faced by families dealing with conditions such as Tourette Syndrome. Learning about effective strategies, like those outlined in this helpful article on strategies to manage Tourette syndrome in children , highlights the importance of proactive planning and support.
Returning to the cyberattack, the incident underscores the need for robust cybersecurity measures to prevent similar crises and ensure the smooth functioning of healthcare services.
Legal and Ethical Implications

Source: rackcdn.com
The Ascension cyberattack, like any major healthcare data breach, raises significant legal and ethical concerns. Healthcare organizations have a complex web of responsibilities to navigate, balancing patient privacy rights with the need to maintain operational efficiency and comply with stringent regulations. Failure to adequately address these issues can result in substantial financial penalties, reputational damage, and erosion of public trust.
Legal responsibilities stem primarily from federal and state regulations like HIPAA in the US, and equivalent laws in other countries. These regulations mandate the implementation of robust security measures to protect Protected Health Information (PHI). A breach necessitates immediate notification to affected individuals, regulatory bodies, and potentially law enforcement. The extent of legal liability hinges on factors such as the organization’s preparedness, response time, and the degree of negligence in security practices.
Failure to comply can lead to hefty fines and even lawsuits from affected patients.
Legal Responsibilities of Healthcare Organizations
Healthcare organizations have a legal obligation to implement and maintain reasonable and appropriate safeguards to protect patient data. This includes risk assessments, data encryption, employee training on security protocols, and incident response plans. Following a cyberattack, these organizations are legally bound to promptly investigate the breach, contain its spread, and notify affected individuals and regulatory agencies as required by law.
Failure to meet these obligations can expose the organization to significant legal repercussions, including civil and criminal penalties. For instance, a hospital failing to adequately secure its EHR system and experiencing a data breach could face substantial fines from regulatory bodies like the Office for Civil Rights (OCR) under HIPAA, as well as class-action lawsuits from affected patients.
Ethical Considerations Related to Patient Privacy and Data Security, Ascension cyberattack impact ehr pharmacy ambulance diversion
Beyond legal mandates, ethical considerations demand a proactive and transparent approach to data security. Patient trust is paramount in healthcare, and a breach can severely damage this trust. Ethical best practices include prioritizing patient well-being, ensuring data minimization (collecting only necessary information), and maintaining transparency throughout the incident response process. Open communication with patients about the breach, its potential impact, and steps taken to mitigate further harm is crucial in rebuilding trust.
For example, an organization could ethically choose to offer credit monitoring services to patients whose financial information was compromised, even if not legally required.
Best Practices for Managing Legal and Ethical Implications
Effective management of legal and ethical implications following a cyberattack requires a multi-faceted approach. Proactive measures, such as regular security audits, employee training, and robust incident response planning, are crucial in mitigating risk. Following a breach, a swift and transparent response is vital. This includes promptly investigating the incident, notifying relevant parties, and providing affected individuals with necessary support and resources.
Maintaining open communication with patients, regulators, and the public helps to build trust and demonstrate accountability. Furthermore, conducting a thorough post-incident review to identify vulnerabilities and implement corrective measures is essential in preventing future breaches. This could include, for example, updating security protocols, strengthening encryption, or investing in advanced security technologies.
Key Legal and Ethical Considerations
| Legal Consideration | Ethical Consideration | Best Practice | Example |
|---|---|---|---|
| HIPAA Compliance (Notification, Breach Response) | Patient Autonomy & Informed Consent | Develop and regularly test a comprehensive incident response plan. | Implementing a plan that includes timely notification to patients and regulatory bodies, as well as providing credit monitoring services. |
| Data Security Standards (NIST Cybersecurity Framework) | Transparency and Accountability | Conduct regular security audits and vulnerability assessments. | Regularly assessing systems for weaknesses and implementing appropriate security measures. |
| Liability for Negligence | Beneficence (acting in the best interest of patients) | Invest in employee training on data security and privacy best practices. | Providing ongoing training to employees on how to handle sensitive patient information and identify phishing attempts. |
| Data Breach Notification Laws (State & Federal) | Respect for Persons (maintaining patient confidentiality) | Establish clear communication protocols for internal and external stakeholders. | Creating a communication plan that Artikels how to interact with patients, the media, and regulatory agencies following a data breach. |
Conclusive Thoughts
The Ascension cyberattack serves as a stark reminder of how vulnerable our healthcare systems are to cyber threats. The interconnectedness of EHRs, pharmacies, and ambulance services means that a single breach can have far-reaching and devastating consequences. While the immediate aftermath involved scrambling to restore systems and mitigate damage, the long-term implications, from financial losses to reputational damage and eroded patient trust, will continue to be felt for years to come.
Learning from this event is crucial; robust cybersecurity measures, proactive risk management, and collaborative efforts across the healthcare sector are paramount to preventing future crises.
FAQ Overview
What type of ransomware was used in the Ascension cyberattack?
The specific type of ransomware used in the Ascension attack hasn’t been publicly disclosed, likely for security reasons.
How many patients were affected by the data breach?
The exact number of patients affected varies depending on the source and the specific data compromised. Official statements from Ascension and news reports offer differing figures.
What compensation did patients receive after the breach?
Information regarding patient compensation is often not publicly released. Details about any settlements or compensation programs would likely be handled privately between Ascension and affected individuals.
What long-term effects did this have on Ascension’s reputation?
The long-term reputational impact is still unfolding. It likely involved a loss of patient trust and potential legal repercussions, though the full extent is difficult to quantify at this time.