Commonspirit Lawsuit Ransomware Attack Class Action
Commonspirit lawsuit ransomware attack class action: The massive data breach at Commonspirit Health sent shockwaves through the healthcare industry and beyond. This wasn’t just another ransomware attack; it exposed the sensitive personal and medical information of millions, leading to a massive class-action lawsuit. We’ll delve into the details of this breach, the legal battles that followed, and the critical questions it raises about data security in the digital age.
Get ready for a deep dive into a story that highlights the vulnerabilities of even the largest healthcare providers.
The timeline of events is chilling. From the initial breach to the data exfiltration and the frantic scramble to contain the damage, the Commonspirit attack unfolded like a real-life thriller. The sheer volume of compromised data—including medical records, financial information, and social security numbers—is staggering. The lawsuit alleges negligence and a failure to implement adequate security measures, raising crucial questions about accountability and the future of data protection in the healthcare sector.
We’ll examine the plaintiffs’ arguments, Commonspirit’s potential defenses, and the broader implications for patients and the industry as a whole.
The Commonspirit Health Ransomware Attack
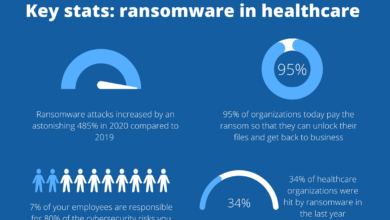
The ransomware attack on Commonspirit Health, a large, non-profit health system, serves as a stark reminder of the vulnerability of healthcare organizations to cyber threats. This incident, unfolding in late 2022, resulted in significant disruption to patient care and raised serious concerns about data security in the healthcare industry. The scale of the breach and the sensitive nature of the compromised data highlighted the critical need for robust cybersecurity measures within healthcare systems.
Timeline of the Commonspirit Health Ransomware Attack
The attack began in late 2022, although the precise date of the initial breach remains undisclosed by Commonspirit Health. The attack involved the deployment of ransomware, encrypting systems and potentially exfiltrating data. The incident was publicly disclosed by Commonspirit Health sometime later, after the organization had begun its investigation and response efforts. The timeline includes the initial compromise of systems, the subsequent data exfiltration, and the lengthy process of restoring systems and notifying affected individuals.
The full extent of the attack and its impact are still unfolding, with ongoing investigations and legal ramifications.
Types of Compromised Data and Impact
The ransomware attack compromised a significant amount of sensitive patient data. While the exact figures are subject to ongoing investigation, reports indicate the potential exposure of millions of records. The following table summarizes the categories of data affected, their estimated impact, and potential mitigation strategies:
| Category of Compromised Data | Estimated Number of Records Affected | Potential Impact | Mitigation Strategies |
|---|---|---|---|
| Patient Names and Addresses | Millions | Identity theft, fraud, stalking | Multi-factor authentication, robust access controls, data encryption |
| Medical Records (including diagnoses, treatments, and test results) | Millions | Medical identity theft, inaccurate medical history, discrimination | Data loss prevention (DLP) tools, regular security audits, employee training |
| Social Security Numbers (SSNs) | Millions | Identity theft, tax fraud, loan fraud | Strict access control, encryption at rest and in transit, regular security assessments |
| Financial Information (e.g., insurance details) | Millions | Financial fraud, identity theft | Payment card industry data security standard (PCI DSS) compliance, regular vulnerability scanning |
Impact on Commonspirit Health’s Operations and Patient Care
The ransomware attack had a significant and immediate impact on Commonspirit Health’s operations and patient care. The encryption of systems disrupted normal hospital functions, leading to delays in patient care, difficulties in accessing medical records, and challenges in scheduling appointments. The attack also resulted in significant financial losses due to downtime, remediation costs, and potential legal liabilities. The disruption caused widespread anxiety and frustration among patients, staff, and the wider community.
The incident highlights the cascading effects of a successful ransomware attack on a healthcare provider, impacting not only the organization itself but also the well-being of its patients and the trust placed in its services.
Legal Ramifications of the Attack
The Commonspirit Health ransomware attack resulted in a significant class action lawsuit, highlighting the complex legal landscape surrounding data breaches and cybersecurity failures. This lawsuit serves as a crucial case study, examining the legal arguments, potential defenses, and broader implications for healthcare organizations and their responsibility to protect patient data.
Key Arguments in the Class Action Lawsuit
The class action lawsuit against Commonspirit Health centers around the plaintiffs’ claims that the company failed to adequately protect their sensitive personal information, leading to the ransomware attack and subsequent data exposure. Plaintiffs argue that Commonspirit’s negligence in maintaining appropriate cybersecurity measures violated various state and federal laws, including those related to data privacy and consumer protection. The core of their argument rests on the assertion that Commonspirit knew or should have known of the vulnerabilities exploited by the attackers and failed to take reasonable steps to mitigate the risks.
This negligence, they contend, directly caused them harm, including emotional distress, identity theft risks, and increased vulnerability to fraud.
The Commonspirit lawsuit, stemming from a devastating ransomware attack, highlights the vulnerability of healthcare systems. This incident underscores the urgent need for robust cybersecurity measures, especially considering the findings of a recent study on the widespread adoption of digital twins in healthcare – check out this insightful piece study widespread digital twins healthcare – which reveals both the potential benefits and increased risks associated with digitalization.
Ultimately, the Commonspirit case serves as a stark reminder of the high stakes involved in protecting sensitive patient data.
Plaintiffs’ Claims and Legal Basis
Plaintiffs’ claims are multifaceted. They allege negligence, breach of contract (in cases where patients had agreements with Commonspirit), breach of fiduciary duty (arguing a responsibility to protect sensitive information), and violations of specific state data breach notification laws. The legal basis for these claims draws upon established legal precedents related to data security, negligence principles, and consumer protection statutes.
The plaintiffs are seeking monetary damages to compensate for the harm suffered as a result of the data breach, including costs associated with credit monitoring, identity theft prevention, and emotional distress.
The Commonspirit lawsuit, stemming from a devastating ransomware attack, highlights the vulnerability of healthcare data. This incident makes me think about the security implications of advancements like those detailed in this article about nuance integrates generative ai scribe epic ehrs , as increased reliance on AI in healthcare could create new attack vectors. Ultimately, robust cybersecurity measures are crucial, especially in light of the Commonspirit class action.
Potential Legal Defenses for Commonspirit Health
Commonspirit Health is likely to raise several defenses. They might argue that they implemented reasonable security measures commensurate with industry standards at the time of the attack, and that the sophistication of the ransomware attack was unforeseeable and unavoidable despite their best efforts. They might also attempt to limit their liability by pointing to the plaintiffs’ own potential contributory negligence or argue that the damages claimed are speculative or not directly causally linked to the breach.
Furthermore, they may argue that the plaintiffs lack standing to sue or that the claims are barred by statute of limitations. The success of these defenses will depend on the evidence presented during the litigation process.
Comparison with Other Significant Ransomware-Related Class Action Lawsuits
Understanding the Commonspirit case requires comparing it to other significant ransomware-related class actions. The following table highlights key differences and similarities:
| Case Name | Key Facts | Outcome | Legal Precedents Set |
|---|---|---|---|
| (Example 1: Insert a real-world case name here, e.g., Doe v. Hospital X) | (Example 1: Briefly describe the facts of the case, e.g., Ransomware attack on a hospital system leading to patient data exposure. Similar to Commonspirit, but potentially involving a different type of healthcare provider or a different ransomware variant.) | (Example 1: Describe the outcome – settlement, dismissal, judgment, etc. Include details such as the amount of settlement if applicable.) | (Example 1: Mention any significant legal precedents established or influenced by the case. For example, did it clarify the standard of care for cybersecurity in healthcare? Did it affect the interpretation of specific state data breach notification laws?) |
| (Example 2: Insert another real-world case name here) | (Example 2: Briefly describe the facts. Highlight differences compared to Commonspirit, such as the size of the organization, the type of data compromised, or the nature of the attack.) | (Example 2: Describe the outcome.) | (Example 2: Mention any significant legal precedents.) |
| (Example 3: Insert another real-world case name here) | (Example 3: Briefly describe the facts. Focus on similarities and differences with Commonspirit and the previous examples.) | (Example 3: Describe the outcome.) | (Example 3: Mention any significant legal precedents.) |
Data Security Practices and Negligence Allegations
The Commonspirit Health ransomware attack exposed serious questions about the adequacy of their data security practices. The lawsuit alleges significant failures in protecting patient data, leading to a massive breach with potentially devastating consequences for affected individuals. Understanding the specifics of these allegations and comparing them to industry best practices is crucial to evaluating the validity of the claims.The lawsuit against Commonspirit Health centers on claims that the organization failed to implement and maintain reasonable security measures to protect sensitive patient data.
These failures, plaintiffs argue, directly contributed to the successful ransomware attack and subsequent data exposure. The core of the negligence claims rests on the assertion that Commonspirit Health breached their duty of care to their patients by not adequately safeguarding their information.
Commonspirit Health’s Data Security Practices
Prior to the attack, the specifics of Commonspirit Health’s data security practices were not publicly available in detail. However, the lawsuit suggests a lack of robust security measures, including insufficient patching of vulnerabilities, inadequate network segmentation, and a possible deficiency in employee security training. The attack itself revealed significant vulnerabilities in their systems, suggesting a lack of proactive security monitoring and incident response planning.
The absence of multi-factor authentication and outdated software are also likely elements of the allegations. The lack of transparency surrounding their security posture before the incident fuels speculation about potential deficiencies.
Allegations of Negligence and Breach of Duty of Care
The plaintiffs allege that Commonspirit Health was negligent in several key areas, including failing to implement reasonable security measures to prevent ransomware attacks, failing to adequately monitor their systems for suspicious activity, and failing to have a comprehensive incident response plan in place. They claim that this negligence directly resulted in the unauthorized access and exfiltration of sensitive patient data, causing significant harm to the affected individuals.
The specific breaches of duty of care include the failure to protect against foreseeable risks, the failure to adequately train employees on cybersecurity best practices, and the failure to implement and maintain effective data backup and recovery systems. The argument is that these failures constitute a breach of the implied contract between the healthcare provider and its patients, where a certain level of data protection is expected.
Comparison with Industry Best Practices
It’s crucial to compare Commonspirit Health’s security protocols (or lack thereof, as alleged) with established industry best practices. The following points highlight potential deficiencies:
The following list Artikels key industry best practices and how Commonspirit Health may have fallen short, based on the lawsuit allegations:
- Regular Security Audits and Penetration Testing: Industry best practice dictates regular security assessments to identify vulnerabilities. The lawsuit suggests a lack of such proactive measures.
- Robust Patch Management: Timely patching of software vulnerabilities is crucial. The attack’s success implies possible neglect in this area.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security. Its absence, as potentially alleged, represents a significant security gap.
- Network Segmentation: Isolating sensitive data from the rest of the network limits the impact of a breach. The extent of network segmentation at Commonspirit Health is unclear, but the breadth of the attack suggests potential deficiencies.
- Employee Security Training: Regular training on phishing and other social engineering tactics is vital. The lawsuit hints at a possible lack of such training.
- Data Encryption: Encrypting data both at rest and in transit minimizes the impact of a successful breach. The effectiveness of Commonspirit Health’s encryption measures, if any, is unknown but the scale of the breach suggests potential shortcomings.
- Comprehensive Incident Response Plan: A well-defined plan is crucial for mitigating the impact of a security incident. The lawsuit implies a lack of such a plan or its inadequate execution.
- Regular Data Backups: Regular backups are essential for data recovery in case of a ransomware attack. The lawsuit’s implications suggest possible shortcomings in this area.
Impact on Patients and Employees
The Commonspirit Health ransomware attack had far-reaching consequences, extending beyond the immediate disruption of services to inflict lasting harm on both patients and employees. The stolen data, potentially including highly sensitive medical records and personal information, created a significant risk of long-term financial and emotional distress for individuals, while also damaging the reputation and stability of the healthcare provider itself.The sheer volume of data compromised necessitates a thorough examination of the potential impacts, extending beyond the immediate aftermath of the attack to encompass the long-term consequences for those affected.
Understanding these impacts is crucial not only for providing support to victims but also for preventing similar incidents in the future.
Patient Impact
The breach of patient data carries significant risks. Identity theft, a major concern following such incidents, involves criminals using stolen information to open fraudulent accounts, apply for loans, or file taxes illegally. Medical identity theft is a particularly insidious form, where perpetrators use stolen medical information to obtain healthcare services or file fraudulent insurance claims, leaving the victim with substantial debt and damaged credit.
Beyond the financial repercussions, victims often experience significant emotional distress, including anxiety, fear, and a sense of violation. The long-term psychological impact can be profound, leading to feelings of helplessness and distrust in healthcare systems. For example, the Equifax breach of 2017 resulted in numerous cases of identity theft and fraud, highlighting the significant and lasting consequences for victims.
Employee Impact
The consequences for Commonspirit Health employees were also substantial. The attack could have led to job losses, either directly through layoffs or indirectly through the financial strain on the organization. Reputational damage, stemming from the perceived failure to protect sensitive data, could affect employees’ career prospects. Furthermore, employees may face legal liabilities, particularly if they are found to have been negligent in their handling of patient data.
For instance, employees might be named in lawsuits brought by affected patients, leading to potential financial and emotional burdens. The stress associated with such a breach, coupled with the potential for legal action, can significantly impact employee well-being and job satisfaction.
Hypothetical Communication Strategy
A proactive and transparent communication strategy could have significantly mitigated the negative impact on both patients and employees. This would involve immediately notifying affected individuals of the breach, clearly outlining the types of data compromised, and providing resources to help them mitigate the risks. For patients, this could include credit monitoring services, identity theft protection, and access to counseling services.
For employees, the strategy should include open communication about the incident, support services to address stress and anxiety, and clear legal guidance. Furthermore, Commonspirit Health could have proactively engaged with law enforcement and regulatory bodies to ensure a swift and thorough investigation. A commitment to improved data security practices, demonstrated through tangible actions and investments, would have further demonstrated responsibility and built trust with stakeholders.
This transparent and empathetic approach would have fostered a sense of accountability and minimized the long-term damage to the organization’s reputation and the well-being of its patients and employees.
The Role of Ransomware Actors and Cyber Insurance

Source: arcpublishing.com
The Commonspirit Health ransomware attack highlights the complex interplay between sophisticated cybercriminals, vulnerable healthcare systems, and the often-debated role of cyber insurance. Understanding the characteristics of the ransomware group and the impact of insurance is crucial to assessing the attack’s overall consequences and preventing future incidents.The identity of the specific ransomware group responsible for the Commonspirit attack may not be publicly known, or may be deliberately obscured.
However, we can analyze the attack based on the typical characteristics of known ransomware operations. Many ransomware groups operate as businesses, employing various tactics to maximize their financial gains. They often target organizations with valuable data, like healthcare providers, knowing that the potential for significant disruption and legal ramifications will incentivize payment. These groups invest in advanced techniques to evade detection, encrypt data effectively, and maintain operational secrecy.
They may also utilize affiliate programs, recruiting less sophisticated actors to deploy their ransomware in exchange for a share of the profits. The specific techniques used in the Commonspirit attack, such as the encryption method, data exfiltration strategy, and ransom demands, would provide valuable clues to the group’s identity and sophistication.
Ransomware Group Characteristics and Tactics
Ransomware groups frequently employ sophisticated techniques, including phishing emails, exploiting software vulnerabilities, and using various forms of social engineering to gain initial access to a network. Once inside, they may move laterally, gaining control of multiple systems before deploying their ransomware. The data encryption process is usually designed to be highly resistant to decryption without the decryption key, held by the ransomware operators.
The Commonspirit lawsuit, stemming from a devastating ransomware attack, highlights the vulnerability of healthcare systems. This vulnerability is especially concerning when considering the already strained resources of rural hospitals, like those discussed in this insightful article on Rural Hospitals Labor Delivery & – the impact of a cyberattack on their limited capacity for essential services, like maternity care, could be catastrophic.
The Commonspirit case underscores the urgent need for better cybersecurity protections across all healthcare facilities, regardless of size or location.
Post-encryption, the group typically demands a ransom payment, often in cryptocurrency, in exchange for the decryption key and sometimes for a promise not to release stolen data. The amount demanded often correlates with the size and sensitivity of the compromised data. The specific tactics used against Commonspirit would require further investigation and potentially access to forensic reports from the incident response team.
The Role of Cyber Insurance in Mitigating Consequences
Cyber insurance plays a multifaceted role in responding to ransomware attacks. For organizations like Commonspirit, a comprehensive cyber insurance policy could cover various expenses incurred during and after the attack. This might include costs associated with incident response, legal fees, regulatory fines, notification costs to affected individuals, credit monitoring services for victims, and potentially even a portion of the ransom payment, depending on the policy’s terms and conditions.
However, the effectiveness of cyber insurance depends heavily on the specifics of the policy, the organization’s preparedness, and the insurer’s response. In some cases, insurers may dispute claims or limit coverage based on policy exclusions or the organization’s failure to meet certain security standards. The Commonspirit case likely involved significant insurance claims, the outcome of which would depend on the details of their policy and the negotiation process with their insurer.
Ethical Implications of Paying Ransoms
The decision to pay a ransom to ransomware actors is fraught with ethical considerations. Paying the ransom directly funds further criminal activity, potentially enabling the group to perpetrate more attacks. It also sets a dangerous precedent, potentially encouraging other attacks against the same or other organizations. Furthermore, there’s no guarantee that paying the ransom will result in the decryption of data or prevent the release of stolen information.
Many security experts advocate against paying ransoms, preferring to focus on robust data backup and recovery strategies, as well as proactive security measures to prevent attacks in the first place. However, the decision to pay often involves a complex risk assessment, weighing the financial and operational consequences of a prolonged outage against the ethical concerns of funding criminal activity.
The Commonspirit case, with its potential impact on patient care and employee data, likely involved a difficult internal debate about the merits of ransom payment.
Future Implications and Prevention Strategies
The Commonspirit Health ransomware attack serves as a stark reminder of the vulnerabilities inherent in the healthcare industry’s digital infrastructure. The incident highlighted not only the devastating financial and reputational consequences but also the potential for significant harm to patient care and employee trust. Learning from this experience is crucial for preventing similar attacks in the future and strengthening the overall cybersecurity posture of healthcare organizations nationwide.
This section will explore key lessons learned and Artikel preventative measures that can significantly mitigate the risk of future ransomware incidents.The attack underscored the urgent need for healthcare providers to prioritize robust cybersecurity practices. Failure to adequately protect sensitive patient data can lead to significant legal liabilities, financial losses, and irreparable damage to an organization’s reputation. Furthermore, the disruption to patient care caused by a ransomware attack can have far-reaching and potentially life-threatening consequences.
A proactive and multi-layered approach to cybersecurity is no longer optional; it’s a necessity.
Key Lessons Learned from the Commonspirit Health Ransomware Attack
The Commonspirit attack revealed several critical vulnerabilities common across the healthcare sector. The attackers exploited weaknesses in the organization’s systems, demonstrating the need for continuous monitoring, vulnerability patching, and employee training. The incident also highlighted the importance of robust incident response planning and the need for strong collaboration with law enforcement and cybersecurity experts during an attack. The lack of sufficient data backups, leading to data loss despite payment of the ransom, underscores the criticality of comprehensive data backup and recovery strategies.
Finally, the attack highlighted the limitations of relying solely on cyber insurance as a primary security measure. Insurance can provide financial assistance, but it does not replace a proactive security posture.
Preventative Measures for Healthcare Providers, Commonspirit lawsuit ransomware attack class action
The following preventative measures can significantly reduce the vulnerability of healthcare providers to ransomware attacks:
- Implement Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of authentication, making it significantly harder for attackers to gain unauthorized access even if they obtain credentials.
- Regular Security Awareness Training for Employees: Educate staff on phishing scams, malware, and other social engineering tactics. Regular training keeps employees updated on the latest threats and reinforces best practices.
- Robust Patch Management: Promptly patch all software and operating systems to address known vulnerabilities. This prevents attackers from exploiting common weaknesses.
- Network Segmentation: Divide the network into smaller, isolated segments to limit the impact of a breach. If one segment is compromised, the rest of the network remains protected.
- Regular Security Audits and Penetration Testing: Conduct regular security assessments to identify vulnerabilities and weaknesses in the system. Penetration testing simulates real-world attacks to expose potential weaknesses before attackers can exploit them.
- Data Backup and Recovery Plan: Implement a robust backup and recovery plan that includes offline backups stored securely in a separate location. This ensures data can be restored even if systems are compromised.
- Endpoint Detection and Response (EDR): Deploy EDR solutions to monitor endpoints for malicious activity and provide real-time threat detection and response capabilities.
- Strong Access Control Policies: Implement strong access control policies that restrict access to sensitive data based on the principle of least privilege. Only authorized personnel should have access to critical systems and data.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan that Artikels steps to take in the event of a ransomware attack. This plan should include communication protocols, data recovery procedures, and collaboration with law enforcement and cybersecurity experts.
Proactive Security Measures to Minimize the Impact of Ransomware Attacks
Proactive security measures are far more effective and cost-efficient than reactive responses. By investing in robust security infrastructure and training, healthcare providers can significantly minimize the likelihood and impact of future ransomware attacks. For example, a hospital that proactively implements MFA, regularly patches its systems, and conducts employee training is far less likely to fall victim to a phishing attack than a hospital that does not.
Furthermore, a robust incident response plan enables a quicker recovery, minimizing downtime and the potential for significant financial losses and reputational damage. The proactive approach shifts the focus from damage control to prevention, significantly improving the overall security posture and protecting both patients and the organization itself. Investing in these measures is not merely a cost; it’s an investment in the long-term security and stability of the healthcare organization.
Closing Notes

Source: bannerbear.com
The Commonspirit Health ransomware attack and subsequent class-action lawsuit serve as a stark reminder of the ever-present threat of cybercrime in the digital age. The scale of the breach, the legal battles, and the lasting impact on patients and employees underscore the urgent need for robust cybersecurity measures in the healthcare industry. While the legal proceedings unfold, one thing is certain: this case will shape future data security practices and the way we think about protecting sensitive information.
The lessons learned here are vital not only for healthcare organizations but for any entity handling sensitive data. It’s a wake-up call we can’t afford to ignore.
FAQ Summary: Commonspirit Lawsuit Ransomware Attack Class Action
What type of ransomware was used in the Commonspirit attack?
The specific type of ransomware used in the attack hasn’t been publicly disclosed by Commonspirit or law enforcement.
What is the estimated cost of the breach to Commonspirit Health?
The exact financial impact, including legal fees, remediation costs, and potential fines, is still being determined.
What compensation might plaintiffs receive in the class-action lawsuit?
The potential compensation will depend on the outcome of the lawsuit and the court’s decision.
Are there similar lawsuits against other healthcare providers following ransomware attacks?
Yes, there have been numerous similar lawsuits against healthcare providers who have experienced ransomware attacks and data breaches.