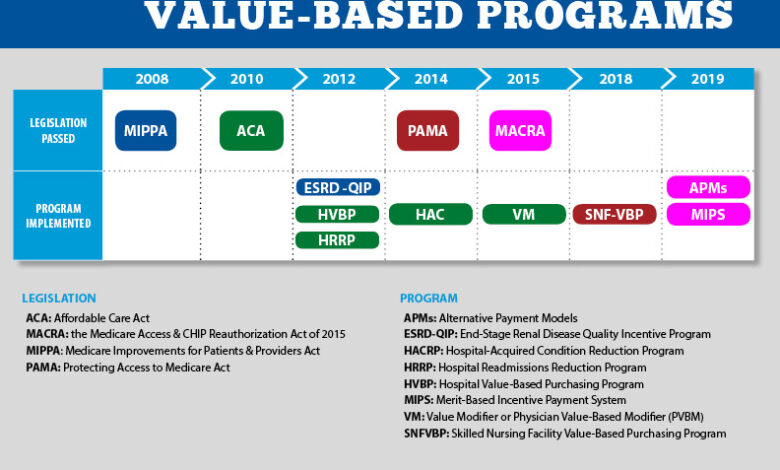
HHS Healthcare Cybersecurity Framework Hospital Requirements & CMS
Hhs healthcare cybersecurity framework hospital requirements cms – HHS Healthcare Cybersecurity Framework hospital requirements and CMS regulations are crucial for protecting patient data and ensuring operational continuity. Navigating this complex landscape can feel overwhelming, but understanding the core components of the framework, aligning with CMS mandates, and implementing robust cybersecurity practices is vital for every hospital. This post breaks down the key aspects, offering insights and practical advice to help hospitals stay secure and compliant.
The HHS framework provides a flexible approach, allowing hospitals to tailor their cybersecurity strategies to their specific risk profiles. Understanding the five core functions – Identify, Protect, Detect, Respond, and Recover – is fundamental. This framework isn’t just about checking boxes; it’s about building a culture of cybersecurity throughout the organization. We’ll explore how hospitals can effectively integrate these requirements with CMS regulations, address common threats, and prepare for potential breaches.
HHS Healthcare Cybersecurity Framework Overview
The Health and Human Services (HHS) Cybersecurity Framework is a voluntary framework designed to help organizations manage and reduce their cybersecurity risks. It’s not a prescriptive checklist but rather a flexible guide adaptable to different healthcare settings and sizes, fostering a risk-based approach to cybersecurity. This framework is particularly crucial for hospitals, given the sensitive nature of patient data and the increasing sophistication of cyber threats.The framework’s core is built upon five interconnected functions: Identify, Protect, Detect, Respond, and Recover.
Each function comprises specific categories and subcategories that provide a structured approach to cybersecurity management. These functions are not sequential; rather, they operate concurrently and iteratively, forming a continuous cycle of risk management. Hospitals can leverage this framework to strengthen their cybersecurity posture, comply with regulations, and ultimately protect patient data and operational integrity.
Key Components of the HHS Cybersecurity Framework
The HHS Cybersecurity Framework is organized around its five core functions, each with specific categories and subcategories that delve into specific cybersecurity activities. These categories provide a detailed roadmap for building a comprehensive cybersecurity program. For instance, the “Identify” function focuses on understanding the organization’s assets, risks, and business environment. The “Protect” function Artikels measures to limit or contain the impact of a cybersecurity incident.
“Detect” focuses on identifying the occurrence of a cybersecurity event. “Respond” details the plan for handling a cybersecurity incident, while “Recover” covers restoring any capabilities or services affected.
Applicability to Hospitals
The HHS Cybersecurity Framework is highly relevant to hospitals due to the sensitive nature of the Protected Health Information (PHI) they handle. Hospitals face unique challenges in cybersecurity, including a large and complex network infrastructure, a diverse workforce with varying levels of cybersecurity awareness, and the increasing prevalence of connected medical devices. The framework provides a structured approach to address these challenges by enabling hospitals to assess their current cybersecurity posture, identify vulnerabilities, and implement appropriate controls.
By adopting the framework, hospitals can significantly improve their ability to protect patient data, maintain operational integrity, and comply with relevant regulations like HIPAA.
Implementation Tiers of the Framework
The framework utilizes a tiered approach to implementation, allowing organizations to tailor their cybersecurity program to their specific risk tolerance and resources. The tiers represent a progression of cybersecurity capabilities, ranging from Tier 1 (partial implementation) to Tier 4 (advanced implementation). Hospitals can choose a tier that aligns with their current capabilities and gradually improve their cybersecurity posture by progressing to higher tiers over time.
This flexibility allows hospitals of varying sizes and resources to benefit from the framework’s guidance. A hospital might start at Tier 1, focusing on fundamental cybersecurity practices, and then gradually progress to higher tiers as their resources and expertise grow.
Comparison of the Five Core Functions
The five core functions of the HHS Cybersecurity Framework are interconnected and crucial for a robust cybersecurity program. The table below provides a comparison of these functions:
| Core Function | Description | Examples | Benefits |
|---|---|---|---|
| Identify | Assess assets, risks, and business environment. | Inventory of systems and data, risk assessments, business impact analysis. | Improved understanding of the organization’s cybersecurity posture. |
| Protect | Develop and implement safeguards to limit or contain the impact of a cybersecurity event. | Access control, data encryption, security awareness training. | Reduced vulnerability to cyber threats. |
| Detect | Identify the occurrence of a cybersecurity event. | Intrusion detection systems, security information and event management (SIEM). | Early detection of cyber threats. |
| Respond | Develop and implement a plan to handle a cybersecurity incident. | Incident response plan, communication plan, forensic analysis. | Effective handling of cybersecurity incidents. |
| Recover | Restore any capabilities or services affected by a cybersecurity incident. | Data backups, disaster recovery plan, business continuity plan. | Minimized downtime and business disruption. |
Hospital Requirements under the HHS Framework
The HHS Cybersecurity Framework provides a voluntary, but highly recommended, set of guidelines for organizations to manage and reduce their cybersecurity risks. For hospitals, adherence to this framework is crucial given the sensitive nature of patient data and the potential consequences of a breach. Failure to implement adequate cybersecurity measures can lead to significant financial penalties, reputational damage, and even legal repercussions.
This section delves into specific requirements and best practices for hospitals under the HHS framework.Hospitals face unique cybersecurity challenges due to the complexity of their IT infrastructure, the sensitive nature of patient data protected by HIPAA, and the increasing sophistication of cyber threats. The framework addresses these challenges by outlining a risk-based approach, encouraging hospitals to identify, assess, manage, and respond to cybersecurity risks effectively.
Understanding these requirements and implementing appropriate measures is paramount to maintaining patient trust and complying with regulatory mandates.
Specific Cybersecurity Requirements for Hospitals
The HHS Cybersecurity Framework is built around five core functions: Identify, Protect, Detect, Respond, and Recover. Each function contains specific cybersecurity requirements that are particularly relevant to hospitals. For instance, under “Identify,” hospitals must inventory their assets, identify their critical systems, and understand their data flow. “Protect” focuses on implementing access controls, data encryption, and security awareness training.
“Detect” emphasizes the need for intrusion detection systems and security information and event management (SIEM) tools. “Respond” Artikels procedures for handling security incidents, including incident reporting and containment. Finally, “Recover” focuses on restoring systems and data after a breach and improving future resilience. The specific requirements within each function are highly detailed and require careful consideration based on the hospital’s unique circumstances and risk profile.
Implications of Non-Compliance, Hhs healthcare cybersecurity framework hospital requirements cms
Non-compliance with the HHS Cybersecurity Framework can have severe consequences for hospitals. The Office for Civil Rights (OCR) within HHS enforces HIPAA, and violations can result in significant financial penalties, ranging from thousands to millions of dollars depending on the severity and nature of the violation. Beyond financial penalties, a data breach can severely damage a hospital’s reputation, leading to a loss of patient trust and potential legal action from affected individuals.
Hospitals may also face operational disruptions, impacting patient care and causing further financial losses. Furthermore, non-compliance can expose the hospital to reputational harm and impact its ability to secure future contracts or funding.
Best Practices for Meeting Requirements
Implementing robust cybersecurity measures requires a multi-faceted approach. This includes regular security assessments and penetration testing to identify vulnerabilities, implementing strong access controls and multi-factor authentication, and providing comprehensive security awareness training for all staff. Hospitals should also invest in advanced security technologies, such as intrusion detection systems, firewalls, and data loss prevention (DLP) tools. Regularly updating software and patching vulnerabilities is also critical.
Furthermore, establishing incident response plans and conducting regular drills are essential for effectively managing and mitigating cybersecurity incidents. Collaboration with external cybersecurity experts can provide valuable insights and support in implementing and maintaining a strong security posture.
The Role of Risk Assessment in Fulfilling Hospital Requirements
Risk assessment is foundational to meeting the requirements of the HHS Cybersecurity Framework. A thorough risk assessment identifies vulnerabilities and potential threats specific to the hospital’s environment. This assessment should consider factors such as the type of data handled, the complexity of the IT infrastructure, and the potential impact of a breach. Based on the risk assessment, hospitals can prioritize security controls and allocate resources effectively to mitigate the most significant risks.
Regularly updating the risk assessment is crucial, as threats and vulnerabilities are constantly evolving. This iterative process ensures that the hospital’s security posture remains aligned with its evolving risk profile. The risk assessment forms the basis for developing a comprehensive cybersecurity plan that addresses the specific needs and vulnerabilities of the hospital.
CMS Regulations and the HHS Framework

Source: thethus.com
Navigating the complex landscape of healthcare cybersecurity requires a clear understanding of the interplay between federal regulations and voluntary frameworks. The Centers for Medicare & Medicaid Services (CMS) sets binding regulations for healthcare providers, while the Department of Health and Human Services (HHS) offers the Cybersecurity Framework (CSF) as a voluntary guidance document. Understanding their similarities and differences is crucial for effective compliance.The CMS regulations primarily focus on protecting patient data and ensuring the security of electronic health information (EHI).
The HHS CSF, conversely, provides a broader, risk-based approach to cybersecurity, applicable across various sectors, including healthcare. While the CSF doesn’t carry the force of law, its adoption demonstrates a commitment to robust cybersecurity practices and can often mitigate the risks associated with non-compliance with CMS regulations.
Overlap Between CMS Regulations and the HHS Framework
Both CMS regulations and the HHS CSF share the common goal of protecting patient data. Many of the CSF’s core functions, such as identifying assets, managing risk, and responding to incidents, directly support compliance with CMS requirements for data security. For instance, the CSF’s emphasis on risk management aligns with CMS’s expectation that providers conduct regular risk assessments and implement appropriate safeguards.
Similarly, the CSF’s incident response function mirrors CMS’s requirements for breach notification and remediation. This overlap means that implementing the HHS CSF can significantly streamline compliance efforts with CMS regulations.
Divergence Between CMS Regulations and the HHS Framework
Despite considerable overlap, differences exist. CMS regulations are prescriptive, outlining specific requirements and controls that must be implemented. The HHS CSF, on the other hand, is more flexible, providing a framework for developing and implementing a tailored cybersecurity program based on an organization’s specific risk profile. This means that while the CSF can guide compliance with CMS regulations, it doesn’t directly replace them.
Hospitals must still meet the specific requirements Artikeld in CMS regulations, even if those requirements are indirectly addressed within the CSF. Furthermore, CMS regulations often focus on specific aspects of data security, such as HIPAA compliance, while the CSF takes a broader view of cybersecurity, encompassing areas like physical security and supply chain risk management.
Ensuring Compliance with Both CMS Regulations and the HHS Framework
Hospitals can ensure compliance with both by adopting a risk-based approach that integrates the HHS CSF into their overall compliance strategy. This involves conducting a thorough risk assessment to identify vulnerabilities and prioritize mitigation efforts. The CSF’s five functions – Identify, Protect, Detect, Respond, and Recover – provide a structured methodology for this process. By mapping specific CMS regulations to the corresponding CSF functions, hospitals can develop a comprehensive cybersecurity program that addresses both the mandatory requirements of CMS and the best practices recommended by the HHS.
This integrated approach not only ensures compliance but also enhances overall cybersecurity posture.
Key Regulations and Framework Requirements
The following list Artikels key areas of overlap and divergence:
- CMS Regulations: HIPAA Security Rule (specifically addressing the administrative, physical, and technical safeguards), HIPAA Breach Notification Rule, Conditions of Participation (CoPs) for hospitals related to information security.
- HHS CSF: Identify (asset management, risk assessment), Protect (access control, data security), Detect (monitoring, intrusion detection), Respond (incident handling, recovery), Recover (business continuity, disaster recovery).
Implementing the HHS CSF can be a powerful tool for demonstrating compliance with CMS regulations, but it is not a substitute for direct adherence to those regulations. A comprehensive strategy that leverages the CSF’s guidance while diligently meeting specific CMS requirements is essential.
Cybersecurity Threats Facing Hospitals
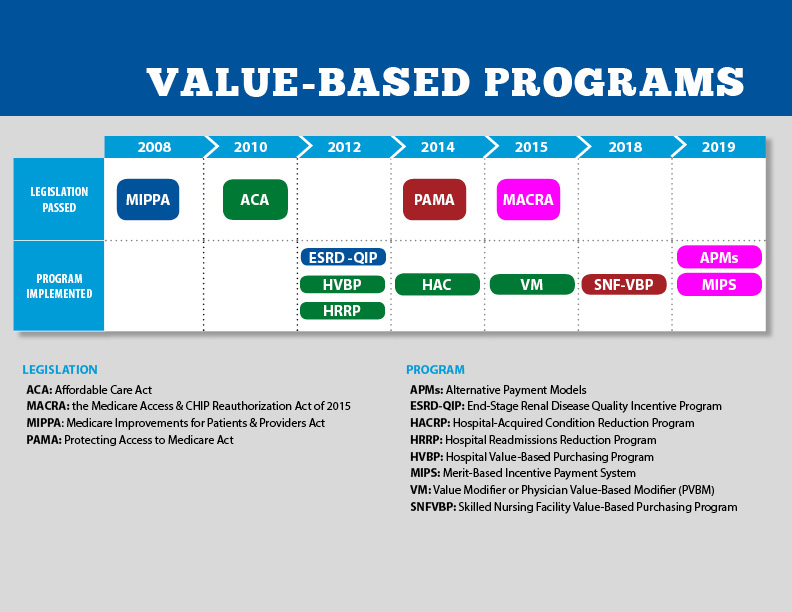
Source: cms.gov
Hospitals are increasingly vulnerable to sophisticated cyberattacks, posing significant risks to patient safety, operational efficiency, and financial stability. The interconnected nature of modern healthcare systems, coupled with the sensitive nature of patient data, creates a lucrative target for malicious actors. Understanding these threats and implementing robust mitigation strategies based on the HHS Cybersecurity Framework is crucial for ensuring the continued safe and effective operation of healthcare facilities.
The potential impact of successful cyberattacks on hospitals can be devastating. Data breaches can expose protected health information (PHI) leading to identity theft, financial fraud, and reputational damage. Disruption of hospital systems can halt essential services, delaying or preventing critical care, and potentially resulting in patient harm or even death. Ransomware attacks can cripple operations, demanding significant financial payouts for the restoration of systems.
The financial and legal consequences can be immense, including fines, lawsuits, and loss of insurance coverage.
Common Cybersecurity Threats Targeting Hospitals
Hospitals face a wide range of cyber threats, including ransomware, phishing attacks, malware infections, denial-of-service (DoS) attacks, and insider threats. Ransomware attacks, in particular, have become increasingly prevalent, encrypting critical data and demanding payment for its release. Phishing emails, often disguised as legitimate communications, can trick employees into revealing sensitive credentials. Malware can compromise systems and steal data, while DoS attacks can overwhelm hospital networks, making them inaccessible.
Insider threats, whether malicious or unintentional, can also pose significant risks.
Impact of Cybersecurity Threats on Patient Data and Operations
The consequences of successful cyberattacks on hospitals extend far beyond financial losses. Breaches of patient data can lead to identity theft, medical identity fraud, and the unauthorized disclosure of sensitive medical information. This can have severe consequences for patients, including financial hardship, emotional distress, and potential harm to their health. Disruption of hospital operations can delay or prevent essential medical procedures, leading to patient harm or even death.
The reputational damage caused by a cyberattack can also impact a hospital’s ability to attract patients and staff. For example, a hospital experiencing a significant data breach might lose the trust of patients, leading to a decline in admissions.
Mitigating Cybersecurity Threats Using the HHS Framework
The HHS Cybersecurity Framework provides a comprehensive approach to managing cybersecurity risks. A robust mitigation strategy should incorporate risk assessment, risk management, and the implementation of appropriate security controls. This includes regular security awareness training for staff, strong password policies, multi-factor authentication, intrusion detection and prevention systems, data loss prevention tools, and regular security audits. The framework emphasizes a continuous improvement cycle, requiring ongoing monitoring and adaptation to evolving threats.
Implementing robust security measures, coupled with regular training and awareness programs for staff, are essential steps in mitigating the risk of cyberattacks. A proactive approach to cybersecurity, based on the HHS Framework’s principles, is far more effective than a reactive one.
Examples of Successful and Unsuccessful Responses to Cyberattacks
Several hospitals have successfully mitigated cyberattacks through proactive security measures and swift incident response plans. These successful responses often involve well-defined incident response teams, robust backup and recovery systems, and close collaboration with law enforcement and cybersecurity experts. Conversely, hospitals that have failed to adequately prepare for cyberattacks have often suffered significant consequences, including substantial financial losses, reputational damage, and patient harm.
For example, a hospital with inadequate backup systems might lose critical patient data during a ransomware attack, leading to significant disruptions in care. Conversely, a hospital with a comprehensive cybersecurity program and a well-trained incident response team may be able to quickly contain a cyberattack, minimizing its impact. These contrasting examples highlight the importance of proactive cybersecurity planning and investment in robust security measures.
Technology and Implementation Strategies
Implementing the HHS Cybersecurity Framework in hospitals requires a robust technological foundation. This goes beyond simply installing software; it necessitates a strategic approach integrating various technologies to achieve comprehensive protection across all hospital systems and data. Successful implementation relies on a multi-layered approach that combines technical solutions with effective policies and procedures.
Security Information and Event Management (SIEM) Systems
SIEM systems are crucial for real-time monitoring and analysis of security events across the hospital’s IT infrastructure. These systems collect logs from various sources – servers, network devices, applications – and correlate them to identify potential threats and security breaches. A well-configured SIEM system can detect anomalies, such as unusual login attempts or data exfiltration, allowing for prompt response and mitigation.
For example, a SIEM might detect a large number of failed login attempts from a single IP address, indicating a potential brute-force attack. The system would then alert security personnel, allowing them to investigate and block the malicious activity before it compromises sensitive data. Effective SIEM implementation involves careful configuration of alerts, regular tuning based on observed events, and integration with other security tools like intrusion detection systems.
The ability to analyze the data produced by the SIEM is also critical; skilled analysts are needed to interpret the alerts and determine the appropriate response.
Security Audits and Penetration Testing
Regular security audits and penetration testing are essential for identifying vulnerabilities in a hospital’s cybersecurity defenses. Security audits involve systematic reviews of security policies, procedures, and technologies to assess their effectiveness. Penetration testing, on the other hand, simulates real-world attacks to identify exploitable weaknesses. These tests can reveal vulnerabilities that might otherwise go unnoticed, allowing for proactive remediation before they can be exploited by malicious actors.
Meeting HHS healthcare cybersecurity framework hospital requirements under CMS guidelines is crucial, especially given the current financial climate. The recent news that Kaiser Permanente nixes 500m Seattle bed tower capital spending highlights how resource allocation impacts even major healthcare systems. This reinforces the need for hospitals to prioritize cybersecurity investments, as breaches can be far more costly than initially anticipated, impacting both financial stability and patient trust.
For instance, a penetration test might reveal a weakness in a web application that allows unauthorized access to patient data. This would then allow the hospital to patch the vulnerability and strengthen its security posture. A combination of internal and external penetration testing provides a more comprehensive assessment, mimicking attacks from both insiders and external threat actors.
The results of these audits and tests should be used to inform improvements to security policies, procedures, and technologies.
Implementing a Security Awareness Training Program
A comprehensive security awareness training program is vital for educating hospital staff about cybersecurity threats and best practices. This program should be tailored to the specific roles and responsibilities of different staff members. Here’s a step-by-step procedure for implementation:
- Needs Assessment: Identify the specific cybersecurity risks faced by the hospital and the knowledge gaps among staff members.
- Curriculum Development: Create training materials that address these risks and knowledge gaps. This might include presentations, videos, and interactive exercises.
- Training Delivery: Deliver the training through a variety of methods, such as online modules, in-person workshops, and phishing simulations.
- Assessment and Feedback: Evaluate the effectiveness of the training through quizzes, surveys, and observation. Gather feedback from staff to improve future training sessions.
- Ongoing Reinforcement: Regularly reinforce the training through email reminders, newsletters, and updates on emerging threats.
- Phishing Simulations: Regularly conduct simulated phishing attacks to test staff awareness and response. This helps identify vulnerabilities and improve staff’s ability to identify and report suspicious emails.
A successful program should cover topics such as phishing, malware, social engineering, password security, and data privacy. Regular refresher training is crucial to keep staff up-to-date on the latest threats and best practices. The program should also include clear reporting mechanisms for suspicious activity. For example, staff should be trained to report any suspicious emails or websites to the IT department immediately.
This proactive approach is essential for minimizing the impact of cyberattacks.
Data Breach Response and Recovery
A data breach in a healthcare setting is a critical event with potentially devastating consequences for patients, the hospital, and its reputation. Effective response and recovery planning are not merely compliance exercises; they are crucial for minimizing damage and ensuring business continuity. This section details the essential steps involved in responding to and recovering from a healthcare data breach.
Incident Response Steps
A well-defined incident response plan is the cornerstone of effective breach management. This plan should Artikel clear roles, responsibilities, and procedures for each stage of the response. The steps involved typically include:
- Detection and Identification: This involves identifying the breach through monitoring systems, security alerts, or reports from staff or patients. Prompt detection is paramount to limiting the impact.
- Containment: Once a breach is confirmed, immediate steps must be taken to isolate the affected systems and prevent further data compromise. This may involve disconnecting affected servers, implementing network segmentation, or disabling user accounts.
- Eradication: This stage focuses on removing the malicious code or threat that caused the breach. This might involve patching vulnerabilities, reinstalling systems, or employing specialized malware removal tools.
- Recovery: This involves restoring systems and data from backups, ensuring the integrity of the data, and validating the effectiveness of the remediation efforts.
- Post-Incident Activity: This crucial phase involves analyzing the breach to identify vulnerabilities, implementing improvements to prevent future incidents, and conducting thorough documentation for regulatory reporting and internal review.
Importance of Incident Reporting
Prompt and accurate reporting of data breaches to regulatory bodies like the HHS Office for Civil Rights (OCR) and potentially state authorities is legally mandated under HIPAA and other regulations. Failure to comply can result in significant fines and reputational damage. Reporting typically involves detailing the nature of the breach, the number of affected individuals, the type of data compromised, and the steps taken to mitigate the impact.
The timeline for reporting varies depending on the specific regulations and the circumstances of the breach. The key is to act quickly and transparently.
Cybersecurity Incident Recovery Process
Recovery from a cybersecurity incident is a multi-faceted process requiring careful planning and execution. It goes beyond simply restoring systems; it involves verifying data integrity, strengthening security measures, and regaining the trust of patients and stakeholders. This process often involves:
- Data Restoration: Restoring data from backups, ensuring data integrity and validating its accuracy.
- System Restoration: Bringing systems back online, ensuring they are secure and functioning correctly.
- Vulnerability Remediation: Identifying and patching vulnerabilities that allowed the breach to occur.
- Security Enhancement: Implementing enhanced security measures to prevent future breaches, such as multi-factor authentication, advanced threat protection, and improved security awareness training for staff.
- Communication and Transparency: Communicating with affected individuals, regulatory bodies, and the public in a timely and transparent manner.
Hypothetical Data Breach Scenario and Remediation
Let’s imagine a scenario where a hospital’s electronic health record (EHR) system is compromised due to a phishing attack targeting a hospital employee. The attacker gains access to sensitive patient data, including names, addresses, medical records, and social security numbers.
The initial response involved immediately disconnecting the affected workstation from the network and initiating a full system scan for malware.
Next, we engaged a cybersecurity incident response team to conduct a forensic investigation, identify the extent of the breach, and determine the attacker’s access methods.
Simultaneously, we began notifying affected patients and initiating the required regulatory reporting process. We also established a dedicated call center to address patient inquiries and concerns.
Following the investigation, we implemented enhanced security measures, including multi-factor authentication for all staff, updated phishing awareness training, and strengthened network security controls.
Finally, we conducted a thorough review of our incident response plan, identifying areas for improvement and updating our procedures accordingly.
Future Trends in Healthcare Cybersecurity
The healthcare landscape is undergoing a rapid digital transformation, bringing with it unprecedented opportunities but also escalating cybersecurity risks. The future of healthcare cybersecurity will be defined by a complex interplay of emerging threats, evolving regulatory landscapes, and the adoption of innovative technologies. Understanding these trends is crucial for hospitals and healthcare providers to proactively safeguard patient data and operational integrity.The convergence of sophisticated cyberattacks and increasingly interconnected medical devices presents a significant challenge.
Navigating the complex HHS healthcare cybersecurity framework and its hospital requirements under CMS can be a real headache. It’s crucial for hospitals to prioritize patient data protection, which reminds me of the importance of managing other complex conditions, like effectively addressing the challenges faced by families dealing with Tourette Syndrome in children – you can find some helpful strategies here: strategies to manage tourette syndrome in children.
Just like safeguarding health data, early intervention and consistent support are key to helping these kids thrive. Returning to the core issue, robust cybersecurity practices are equally vital for maintaining patient trust and ensuring the smooth operation of hospitals under the CMS guidelines.
We’re moving beyond simple ransomware attacks to more targeted, data exfiltration campaigns aimed at stealing sensitive patient information for financial gain or even to disrupt critical care operations. This necessitates a multi-layered, proactive approach to security, moving beyond reactive measures.
Navigating the complex HHS healthcare cybersecurity framework and CMS hospital requirements can feel overwhelming, especially when considering the sensitive data involved. But improving patient care often means embracing new technologies, and that’s where a shift in thinking is needed; check out this article on reimagining collaboration in senior care a technology driven approach for some innovative ideas.
Ultimately, strong cybersecurity practices remain crucial, even as we leverage technology for better senior care, to ensure compliance with the HHS framework and CMS regulations.
Emerging Cybersecurity Threats and Vulnerabilities
The threat landscape is constantly evolving. We’re seeing a rise in AI-powered attacks that can automate and scale malicious activities, making them harder to detect and respond to. Furthermore, the increasing reliance on Internet of Medical Things (IoMT) devices introduces numerous vulnerabilities, particularly in poorly secured or outdated equipment. Sophisticated phishing campaigns, exploiting the human element, remain a persistent threat, often targeting hospital staff with access to sensitive systems.
Exploiting zero-day vulnerabilities in medical devices is another growing concern, requiring constant vigilance and rapid patching. Finally, the increasing use of cloud services for storing and processing sensitive patient data presents new challenges related to data privacy and security in third-party environments.
The Future Direction of the HHS Cybersecurity Framework
The HHS Cybersecurity Framework is likely to evolve to incorporate the latest threats and technologies. We can expect a greater emphasis on proactive risk management, incorporating AI-driven threat detection and response capabilities. The framework will likely place a stronger focus on the security of IoMT devices, requiring stricter guidelines for their deployment and management within hospital networks. Increased collaboration and information sharing between healthcare organizations, government agencies, and cybersecurity vendors will be crucial.
Furthermore, we can anticipate a greater focus on supply chain security, addressing vulnerabilities introduced by third-party vendors and software components. The framework will likely need to adapt to accommodate the increasing use of cloud-based services, establishing clear guidelines for data security and compliance in these environments.
The Impact of AI and IoT on Hospital Cybersecurity
Artificial intelligence offers significant potential for enhancing healthcare cybersecurity. AI-powered tools can analyze vast amounts of data to identify anomalies and potential threats in real-time, enabling faster and more effective responses. However, AI also presents new vulnerabilities. AI algorithms themselves can be targeted by adversarial attacks, potentially compromising their effectiveness. The increased reliance on IoMT devices, while offering benefits in patient care, creates a larger attack surface.
These devices often lack robust security features and are frequently connected to hospital networks with limited security controls. The sheer volume of data generated by IoMT devices also presents challenges for security monitoring and incident response. AI-driven threat hunting and response systems can help mitigate these challenges, but a comprehensive security strategy that addresses both the opportunities and vulnerabilities presented by AI and IoT is essential.
Visual Representation of the Evolution of Healthcare Cybersecurity Threats
Imagine a graph with the X-axis representing the years (2013-2023) and the Y-axis representing the sophistication and frequency of cyberattacks. The graph begins in 2013 with relatively simple attacks like phishing and malware targeting individual computers. The line gradually increases in slope, reflecting the increasing sophistication of attacks over the years. Around 2016-2017, the line shows a steeper incline, representing the rise of ransomware attacks targeting hospitals.
By 2019-2020, the line shows a more erratic pattern, reflecting the emergence of more sophisticated attacks, including AI-powered attacks and targeted data exfiltration campaigns. The line continues to rise sharply in the final years, representing the growing threat posed by IoT vulnerabilities and the increasing complexity of the healthcare IT ecosystem. The graph could also include different colored lines to represent different attack vectors (e.g., ransomware, phishing, data breaches).
This visual representation would illustrate the evolution of healthcare cybersecurity threats from relatively simple attacks to highly sophisticated and targeted campaigns.
Outcome Summary: Hhs Healthcare Cybersecurity Framework Hospital Requirements Cms
Successfully navigating the complexities of the HHS Healthcare Cybersecurity Framework and CMS regulations requires a proactive and multi-faceted approach. By understanding the framework’s core functions, prioritizing risk assessment, investing in appropriate technology, and fostering a strong security culture among staff, hospitals can significantly enhance their cybersecurity posture. Remember, it’s not just about compliance; it’s about safeguarding sensitive patient data and maintaining operational resilience in the face of evolving cyber threats.
Staying informed and adapting to the ever-changing threat landscape is key to long-term success.
FAQ Guide
What are the penalties for non-compliance with the HHS Cybersecurity Framework?
Penalties vary depending on the severity of the non-compliance and can include financial fines, reputational damage, loss of patient trust, and potential legal action.
How often should hospitals conduct security audits and penetration testing?
The frequency of audits and penetration testing should be determined based on risk assessment, but generally, annual audits and at least semi-annual penetration testing are recommended.
What is the role of a Chief Information Security Officer (CISO) in a hospital?
The CISO is responsible for overseeing all aspects of the hospital’s cybersecurity program, including strategy development, implementation, and compliance.
How can hospitals train staff on cybersecurity awareness effectively?
Effective training involves a combination of online modules, hands-on workshops, regular updates, and simulated phishing exercises to keep staff engaged and informed.





