Maintaining Inbound Chain of Custody for Hospitals
Maintaining an inbound chain of custody for hospitals is crucial. Think about it – every single item, from life-saving pharmaceuticals to delicate medical devices, needs a meticulously tracked journey from supplier to patient care. This isn’t just about paperwork; it’s about patient safety, regulatory compliance, and ensuring the integrity of every medical intervention. This post dives deep into the nuts and bolts of building a robust inbound chain of custody system in a hospital setting, covering everything from documentation to technology and risk management.
We’ll explore the key players involved, the essential documentation required, and the technologies that can streamline the process. We’ll also tackle the challenges – security breaches, regulatory hurdles, and the ever-present risk of human error – and how to mitigate them effectively. Ultimately, the goal is to create a system that’s not just compliant, but efficient and reliable, ensuring that every element of patient care is supported by a trustworthy and transparent supply chain.
Defining Inbound Chain of Custody in Hospitals
Maintaining a robust inbound chain of custody is critical for patient safety and the legal integrity of a hospital. It ensures that all materials entering the hospital, from pharmaceuticals to medical devices, are properly identified, tracked, and accounted for throughout their journey from the supplier to the point of use. This meticulous tracking minimizes the risk of errors, contamination, and fraud, ultimately contributing to better patient outcomes and operational efficiency.Inbound chain of custody in a hospital refers to the documented process of tracking and verifying the origin, handling, and storage of materials received by the hospital.
This rigorous system safeguards against the introduction of counterfeit, expired, or compromised products, preventing potential harm to patients and upholding the hospital’s legal and ethical responsibilities. The process ensures accountability at each stage, providing a verifiable audit trail should any discrepancies arise.
Key Stakeholders in Inbound Chain of Custody
The effective management of inbound chain of custody requires collaboration among several key stakeholders. These individuals and departments play vital roles in ensuring the integrity of the process from start to finish. Their coordinated efforts are essential for maintaining a reliable and verifiable record of each material’s journey.
- Receiving Department: Responsible for initial inspection, verification against purchase orders, and logging of incoming materials.
- Supply Chain Management: Oversees the entire procurement process, including vendor selection and contract negotiation, ensuring adherence to quality standards and regulatory compliance.
- Pharmacy: Manages the inbound chain of custody for pharmaceuticals, ensuring proper storage, handling, and dispensing.
- Medical Device Department: Responsible for the tracking and management of medical devices, including verification of authenticity and functionality.
- Laboratory: Handles the inbound chain of custody for blood products and other biological samples, maintaining strict temperature and handling protocols.
- Quality Assurance/Risk Management: Monitors the entire process, audits records, and identifies areas for improvement.
Examples of Materials Requiring Inbound Chain of Custody Tracking
A wide range of materials necessitate rigorous inbound chain of custody tracking within a hospital setting. The importance of tracking stems from the potential risks associated with compromised materials, impacting both patient safety and the hospital’s legal standing. Accurate tracking prevents errors and ensures the quality and integrity of the materials used in patient care.
- Pharmaceuticals: Tracking prevents the use of counterfeit or expired medications.
- Medical Devices: Verification ensures proper functionality and prevents the use of recalled or substandard devices.
- Blood Products: Maintaining a strict chain of custody is critical for ensuring the safety and efficacy of blood transfusions.
- Implants: Accurate tracking ensures the correct implant is used and prevents surgical errors.
- Biological Samples: Proper tracking is essential for maintaining the integrity of laboratory tests and research.
Flowchart Illustrating the Typical Inbound Chain of Custody Process
The following describes a typical inbound chain of custody process, visualized as a flowchart. This process ensures accountability and traceability at each step, minimizing the risk of errors or discrepancies. The detailed steps Artikeld provide a clear understanding of how materials are tracked from their origin to their final destination within the hospital.Imagine a flowchart with the following steps:
1. Order Placement The hospital places an order for supplies with a verified vendor.
2. Shipment The vendor ships the materials, including a packing slip and any required documentation.
3. Receiving The hospital’s receiving department receives the shipment and verifies the contents against the purchase order and packing slip. Any discrepancies are immediately reported.
Maintaining a tight inbound chain of custody in hospitals is crucial for patient safety and legal compliance. This becomes even more critical when considering the potential of advanced technologies; for instance, a recent study on the widespread use of digital twins in healthcare, which you can read about here: study widespread digital twins healthcare , highlights the need for robust tracking systems.
Ultimately, a clear chain of custody ensures accountability and minimizes risks associated with medical supplies and patient data.
4. Inspection Materials are inspected for damage or signs of tampering. Temperature-sensitive items are checked for proper temperature maintenance.
5. Verification Serial numbers, lot numbers, and expiration dates are verified against the accompanying documentation.
6. Acceptance If everything is in order, the materials are accepted and logged into the hospital’s inventory system. A unique tracking number is assigned.
7. Storage Materials are stored in designated areas according to their specific requirements (temperature, humidity, etc.).
8. Distribution When needed, materials are retrieved from storage and distributed to the appropriate departments, with proper documentation and tracking maintained.
9. Usage/Disposal After use, materials are disposed of according to hospital protocols, with appropriate documentation maintained.
Documentation and Record-Keeping Procedures

Source: realtimenetworks.com
Maintaining meticulous documentation is the cornerstone of a robust inbound chain of custody system in hospitals. Accurate and complete records ensure the traceability of all incoming materials, from pharmaceuticals and medical devices to lab samples and supplies. This traceability is critical for patient safety, regulatory compliance, and efficient inventory management. Any lapse in documentation can lead to serious consequences, impacting everything from treatment efficacy to legal liability.
Best practices dictate a multi-layered approach to documentation, combining paper-based logs with potentially electronic systems for enhanced security and accessibility. This ensures a clear audit trail, allowing for easy verification of the journey of each item from the supplier to its final destination within the hospital. Each step in the process, from receipt to storage, must be documented precisely and promptly.
Inbound Chain of Custody Log Template
A standardized log is essential for consistent record-keeping. The following template provides a framework, which can be adapted to fit specific hospital needs and regulatory requirements. Remember to tailor it to include any unique identifiers or tracking numbers used within your institution.
| Date | Time | Supplier Name | Supplier Contact Information | Material Description | Quantity Received | Lot/Batch Number | Expiration Date (if applicable) | Condition Upon Receipt (e.g., undamaged, damaged) | Received By (Name & Signature) | Witness (Name & Signature, if applicable) | Tracking Number (if applicable) | Storage Location |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| MM/DD/YYYY | HH:MM |
Examples of Documentation Errors and Consequences
Inaccurate or incomplete documentation can have far-reaching consequences. For instance, failing to record the quantity received could lead to shortages, compromising patient care. Incorrectly recording the expiration date of a medication could result in the administration of expired drugs, posing a serious risk to patient safety. A missing signature could cast doubt on the authenticity of the received materials, potentially leading to legal complications or recalls.
Even seemingly minor errors, such as omitting the lot number, can hinder effective tracking and investigation in the event of a recall or adverse event. These issues underscore the importance of rigorous attention to detail in all aspects of documentation.
Importance of Tamper-Evident Seals and Labels
Tamper-evident seals and labels provide an extra layer of security, visually indicating if a package has been opened or compromised during transit or storage. These seals, often employing unique markings or destructible materials, offer immediate visual confirmation of any unauthorized access. The use of tamper-evident seals is especially crucial for high-value or sensitive materials, such as pharmaceuticals or controlled substances.
Their presence provides an additional check on the integrity of the inbound chain of custody, bolstering confidence in the authenticity and safety of the received materials. Documentation should explicitly note the presence and condition of these seals upon receipt.
Security and Access Control Measures
Maintaining a secure inbound chain of custody for hospital materials is paramount to patient safety, regulatory compliance, and the overall integrity of operations. A compromised chain of custody can lead to significant risks, including the use of counterfeit or substandard medical supplies, potential for medication errors, and legal repercussions. Robust security and access control measures are therefore essential.Security risks associated with a compromised inbound chain of custody are multifaceted.
Compromised materials could range from pharmaceuticals and medical devices to lab reagents and blood products. The consequences of using compromised materials vary depending on the specific item, but generally include potential harm to patients, financial losses due to wasted resources, and reputational damage to the hospital. Furthermore, a breach could lead to legal action and regulatory penalties.
Securing Storage Areas for Sensitive Materials
Secure storage areas require a multi-layered approach. This begins with physically secure locations, ideally equipped with features like reinforced doors, alarm systems, and surveillance cameras. Environmental controls are also critical; temperature and humidity-sensitive materials require specific storage conditions to maintain their integrity and efficacy. Access to these areas should be strictly limited to authorized personnel, and regular audits should be conducted to ensure the effectiveness of security measures.
For example, a hospital might utilize a dedicated, locked pharmacy vault for high-risk medications, complete with biometric access control and real-time monitoring. Similarly, a climate-controlled storage room with access logs could be designated for sensitive diagnostic reagents.
Controlled Access to Inventory and Materials
A well-defined system for controlled access is vital. This necessitates a robust inventory management system that tracks the movement of all materials throughout the inbound chain of custody. Each item should be uniquely identified with a tracking number, and its location and status should be recorded at every stage, from receipt to storage to dispensing. Access to inventory should be granted only to authorized personnel, with their access privileges carefully defined and regularly reviewed.
This could involve the use of electronic access cards, biometric scanners, or a combination of both, linked to a central access control system that logs all activity.
Physical and Electronic Security Measures
Physical security measures include secured storage areas, surveillance systems (CCTV), alarm systems, and physical access controls (e.g., key card readers, locks). Electronic security measures are equally crucial. These include electronic inventory management systems with real-time tracking capabilities, access control systems that log all entries and exits, and digital signatures or electronic authentication for verifying the integrity of delivery documentation.
For instance, a hospital might use RFID tags on high-value medical devices to track their movement within the facility, and an electronic logbook to record the transfer of custody between personnel. Regular software updates and cybersecurity protocols are also critical to prevent unauthorized access and data breaches.
Maintaining a tight inbound chain of custody in hospitals is crucial for patient safety and legal compliance. Accurate record-keeping is paramount, and this is where technology like AI can help. The integration of AI, as seen in the recent news about nuance integrates generative ai scribe epic ehrs , offers potential for streamlining documentation and reducing errors, ultimately strengthening the overall chain of custody process within the hospital setting.
This improved accuracy directly benefits the secure management of patient information.
Technology and Automation in Chain of Custody Management: Maintaining An Inbound Chain Of Custody For Hospitals
Implementing technology in hospital inbound chain of custody dramatically improves efficiency, accuracy, and security. Manual processes are prone to human error and lack the real-time tracking capabilities crucial for maintaining the integrity of medical samples and supplies. Automation minimizes these risks and provides a more robust system.
Barcode Scanning and RFID Technology for Chain of Custody Tracking
Barcode scanning and Radio-Frequency Identification (RFID) technology offer significant advantages in tracking items throughout the inbound chain of custody. Barcode scanners allow for quick and accurate identification of each item, recording its entry into the system with minimal manual input. This reduces the risk of transcription errors and speeds up the entire process. RFID tags, on the other hand, provide a more hands-off approach, automatically logging the location and movement of tagged items.
This is particularly beneficial for high-volume environments or situations where manual scanning might be impractical or time-consuming. For instance, imagine a large pallet of medical supplies arriving – RFID technology would automatically register each item’s arrival, reducing the labor and potential for human error involved in individual barcode scanning. The data collected through both methods feeds directly into the chain of custody management system, providing a comprehensive and auditable record.
Benefits of Dedicated Software for Managing Inbound Chain of Custody
Dedicated software solutions provide a centralized system for managing the entire inbound chain of custody process. These systems typically offer features such as automated alerts for expiring items, real-time tracking of item location, and detailed audit trails. This level of control ensures compliance with regulatory requirements and minimizes the risk of errors or discrepancies. Moreover, dedicated software often integrates with existing hospital systems, streamlining workflows and reducing administrative burden.
For example, a system might automatically update inventory levels upon item receipt, eliminating the need for manual data entry. The ability to generate comprehensive reports also aids in performance monitoring and identifying areas for improvement within the chain of custody process. The improved visibility and control offered by such software ultimately enhance patient safety and operational efficiency.
Comparison of Software Solutions for Chain of Custody Management
Several software solutions cater specifically to chain of custody management in healthcare settings. The optimal choice depends on the hospital’s specific needs and budget. Features to consider include ease of use, integration capabilities with existing systems (like Electronic Health Records – EHRs), reporting functionalities, and scalability. The pricing model (subscription-based, one-time purchase, etc.) is also a critical factor.
| Software Name | Key Features | Integration Capabilities | Pricing Model |
|---|---|---|---|
| MedTrack Chain of Custody | Real-time tracking, automated alerts, audit trails, customizable workflows, mobile accessibility. | EHR integration, laboratory information systems (LIS) integration. | Subscription-based, tiered pricing. |
| ChainSafe | Secure data storage, barcode and RFID compatibility, robust reporting, user role management. | HL7 integration, various LIMS integrations. | One-time purchase, additional fees for support and training. |
| CustodianPro | Simple interface, basic tracking features, good for smaller facilities. | Limited integration capabilities. | One-time purchase, affordable option. |
Compliance and Regulatory Requirements
Maintaining a robust inbound chain of custody in a hospital setting isn’t just about operational efficiency; it’s a critical component of legal and ethical compliance. Failure to adhere to relevant regulations can lead to severe consequences, impacting patient safety, legal liability, and the hospital’s reputation. This section Artikels key regulations and strategies for ensuring compliance.
Hospitals face a complex web of regulations impacting the handling of inbound materials, from pharmaceuticals and medical devices to lab specimens and biological samples. Non-compliance can result in hefty fines, legal action, suspension of licenses, and damage to public trust. Proactive compliance strategies are therefore essential for protecting the hospital and its patients.
Relevant Regulations and Standards
Several key regulations and standards govern inbound chain of custody in hospitals. The Food and Drug Administration (FDA) sets stringent requirements for the handling and tracking of pharmaceuticals and medical devices, emphasizing the importance of maintaining an unbroken chain of custody to ensure product authenticity and safety. The Health Insurance Portability and Accountability Act (HIPAA) plays a crucial role in protecting patient health information, including data associated with samples and specimens.
Maintaining a tight inbound chain of custody is crucial for any hospital, ensuring the integrity of medical supplies and patient records. This is especially vital in areas with limited resources, like those served by rural hospitals, where efficient processes are paramount. The challenges faced by these facilities are highlighted in this insightful article on Rural Hospitals Labor Delivery & , underscoring the need for robust systems to manage materials effectively.
Ultimately, a strong inbound chain of custody contributes to better patient care and operational efficiency in all hospital settings.
Other relevant regulations might include state-specific licensing requirements and those related to controlled substances. Compliance demands a thorough understanding and implementation of all applicable regulations.
Implications of Non-Compliance
Non-compliance with these regulations can have far-reaching and severe consequences. For example, a breach in the chain of custody for a pharmaceutical product could lead to the administration of counterfeit or adulterated drugs, resulting in serious patient harm and potential legal liability for the hospital. Similarly, a failure to properly secure and track patient samples could violate HIPAA regulations, leading to significant fines and reputational damage.
The severity of penalties can vary depending on the nature and extent of the violation, but the potential risks are substantial.
Strategies for Maintaining Compliance
Successful compliance relies on a multi-pronged approach. This includes establishing clear procedures for receiving, documenting, and storing inbound materials; implementing robust security measures to prevent unauthorized access or tampering; and providing comprehensive training to all staff involved in handling these materials. Regular internal audits and staff training are crucial to ensure procedures are followed consistently. Investing in technology solutions, such as barcode scanning and electronic tracking systems, can significantly enhance traceability and accountability.
Furthermore, maintaining detailed and accurate records is essential for demonstrating compliance during audits or investigations. A strong culture of compliance, fostered by leadership commitment and ongoing staff education, is fundamental to success.
Importance of Regular Audits and Internal Reviews
Regular audits and internal reviews are not merely compliance exercises; they are vital tools for identifying weaknesses and improving the chain of custody system. These reviews should cover all aspects of the process, from receiving and inspection to storage and disposal. Audits should assess the effectiveness of existing procedures, identify areas for improvement, and ensure that all staff members are adequately trained and compliant.
The findings of these reviews should be documented, and corrective actions implemented promptly. By proactively identifying and addressing potential vulnerabilities, hospitals can significantly reduce the risk of non-compliance and safeguard patient safety.
Training and Staff Education
Effective chain of custody procedures rely heavily on well-trained staff. A comprehensive training program is crucial to ensure consistent adherence to protocols and minimize the risk of errors that could compromise the integrity of samples and potentially impact patient care. This program must cover all aspects of handling inbound materials, from initial receipt to final storage.A multi-faceted approach is needed, encompassing initial training, regular refresher courses, and readily available resources for ongoing reference.
This ensures staff remain proficient and up-to-date with the latest regulations and best practices. The program should be tailored to the specific roles and responsibilities of different staff members, ensuring that everyone receives training relevant to their tasks.
Training Program Design
The training program should be modular, allowing for flexibility in delivery and accommodating varying levels of experience. It should incorporate a mix of methods, including interactive lectures, hands-on simulations, and case studies to enhance learning and retention. Modules could cover topics such as proper identification and verification procedures, secure storage and handling techniques, documentation best practices, and the consequences of non-compliance.
Regular quizzes and assessments can be incorporated to evaluate comprehension and identify areas needing further clarification. Finally, the program should incorporate a feedback mechanism allowing staff to express concerns and suggest improvements.
Staff Checklist for Receiving and Handling Materials
A comprehensive checklist is essential to ensure consistency and completeness in handling inbound materials. This checklist should be easily accessible and should guide staff through each step of the process. It should include sections on: verifying the identity of the sender and recipient, confirming the integrity of the packaging, noting any discrepancies or damage, recording the date and time of receipt, assigning a unique identification number, securing the materials appropriately, and documenting all actions taken.
This checklist should be integrated into the hospital’s existing procedures and readily available to all relevant personnel.
Effective Communication Strategies
Clear and consistent communication is paramount to reinforce chain of custody protocols. Regular staff meetings and email updates can be used to disseminate important information, address common challenges, and reinforce best practices. Visual aids, such as posters and infographics summarizing key procedures, can be strategically placed in high-traffic areas to serve as constant reminders. The hospital could also utilize a dedicated intranet page or online portal to share resources, updates, and training materials.
Finally, incorporating chain of custody procedures into regular performance reviews and feedback sessions can further reinforce their importance.
Ongoing Training and Updates
The healthcare landscape is constantly evolving, with new regulations and best practices regularly emerging. Therefore, ongoing training and updates are critical to maintaining compliance and ensuring the continued effectiveness of chain of custody procedures. Regular refresher courses should be implemented, ideally annually, to reinforce key concepts and address any changes in regulations or procedures. Staff should also be encouraged to participate in relevant professional development opportunities and workshops to stay abreast of industry advancements.
Access to updated policy documents and readily available resources is also essential to ensure staff have the information they need to perform their duties effectively.
Risk Management and Mitigation Strategies
Maintaining a secure inbound chain of custody in a hospital setting requires a proactive approach to risk management. Failure to adequately address potential vulnerabilities can lead to compromised patient safety, legal repercussions, and damage to the hospital’s reputation. A robust risk management plan is essential to mitigate these risks and ensure the integrity of the process.Potential risks span various areas, from human error to sophisticated cyberattacks.
A comprehensive strategy involves identifying these risks, assessing their likelihood and impact, and implementing appropriate mitigation strategies. This process should be regularly reviewed and updated to reflect changes in technology, regulations, and the hospital’s operational environment.
Risk Assessment Matrix
A risk assessment matrix provides a structured approach to prioritizing risks. This matrix typically uses a two-dimensional table, with one axis representing the likelihood of a risk occurring (e.g., low, medium, high) and the other axis representing the potential impact of the risk (e.g., minor, moderate, major, catastrophic). Each identified risk is then plotted on the matrix, allowing for prioritization based on its overall risk score (likelihood x impact).
For example, a risk of unauthorized access to medical samples with high likelihood and major impact would receive a high priority, demanding immediate attention. Risks are then categorized by severity and assigned mitigation strategies based on their priority.
Mitigation Strategies
Mitigation strategies encompass both preventative and corrective actions. Preventative measures aim to reduce the likelihood of a risk occurring, while corrective actions focus on minimizing the impact if a risk does materialize.
- Preventative Measures: Examples include implementing strict access control protocols (e.g., using biometric scanners, requiring multiple authorizations), regular staff training on chain of custody procedures, employing robust data encryption techniques for electronic records, and conducting regular audits of the chain of custody process.
- Corrective Actions: These actions are taken in response to a risk event. For example, a breach of security might trigger an immediate investigation, involving tracing the compromised samples, notifying relevant authorities, and implementing immediate security enhancements to prevent recurrence. A detailed incident report would be compiled, documenting the event, its impact, and the corrective actions taken.
Incident Response Plans
A well-defined incident response plan is crucial for effectively managing chain of custody breaches. The plan should Artikel clear steps to be taken in the event of a security breach or other incident affecting the integrity of the chain of custody. This includes:
- Immediate Actions: Securing the affected area, preventing further access to compromised materials, and notifying relevant personnel (e.g., security, IT, legal).
- Investigation: Conducting a thorough investigation to determine the cause of the breach, the extent of the compromise, and the individuals involved.
- Containment: Implementing measures to contain the damage and prevent further compromise.
- Recovery: Restoring the chain of custody to its pre-breach state, including any necessary remediation steps.
- Post-Incident Review: Conducting a post-incident review to identify areas for improvement in the chain of custody process and update the risk management plan accordingly.
For instance, a hospital might discover a missing sample. The incident response plan would dictate immediate actions like securing the storage area, initiating an internal investigation, and possibly involving law enforcement depending on the circumstances. The investigation would aim to determine whether the sample was stolen, misplaced, or destroyed, and would include reviewing security footage and interviewing relevant personnel.
Corrective actions might include improving inventory management, enhancing security measures, and retraining staff on proper sample handling procedures. A comprehensive report documenting the entire incident and its resolution would be maintained for future reference and improvement.
Continuous Improvement and Monitoring
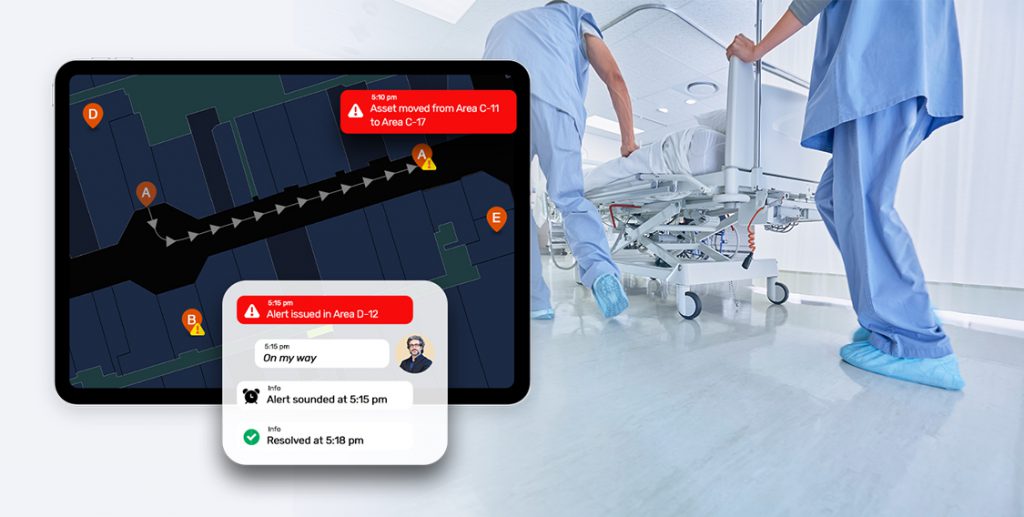
Source: googleusercontent.com
Maintaining a robust inbound chain of custody system in a hospital setting isn’t a one-time effort; it requires ongoing vigilance and a commitment to continuous improvement. Regular monitoring and evaluation are crucial to ensure the system remains effective, reliable, and compliant with all relevant regulations. This involves a multifaceted approach encompassing data analysis, performance tracking, and procedural review.Regular monitoring of the inbound chain of custody system is essential to identify weaknesses and ensure the system’s effectiveness in maintaining the integrity of samples and specimens.
This involves tracking key performance indicators (KPIs), analyzing data to identify trends and areas for improvement, and regularly reviewing and updating procedures.
Key Performance Indicators (KPIs) for Chain of Custody, Maintaining an inbound chain of custody for hospitals
Effective monitoring relies on the strategic use of KPIs. These quantifiable metrics provide insights into system performance, highlighting areas needing attention. For example, tracking the number of discrepancies found during sample verification, the time taken to process samples from receipt to testing, and the rate of lost or damaged samples can reveal potential bottlenecks or vulnerabilities. A high discrepancy rate might indicate insufficient staff training or inadequate documentation procedures.
Long processing times could suggest inefficiencies in workflow or a lack of automation. A high rate of lost or damaged samples indicates a need for improvements in handling and storage procedures. By regularly monitoring these KPIs, hospital administrators can identify trends and implement targeted improvements. For instance, if the time to process samples consistently exceeds the target, an investigation might reveal a need for additional staff or the implementation of a more streamlined workflow.
Data Analysis for System Improvement
Analyzing data collected through KPI tracking is crucial for identifying areas needing improvement. This might involve using statistical process control charts to monitor trends in key metrics, or conducting root cause analyses to investigate specific incidents of sample mishandling or loss. For instance, a sudden spike in the number of discrepancies could be analyzed to determine its underlying cause, which might be a new batch of faulty equipment or a change in staff training protocols.
This data-driven approach allows for targeted interventions, ensuring resources are allocated effectively to address the most pressing issues. For example, if data reveals a significant number of errors related to sample labeling, additional training on proper labeling techniques can be implemented.
Regular Review and Update of Chain of Custody Procedures
A formal process for regularly reviewing and updating chain of custody procedures is essential to maintain the system’s effectiveness and compliance. This should involve a multidisciplinary team comprising personnel from relevant departments, such as laboratory staff, nursing staff, and administrative personnel. The review should consider changes in technology, regulations, and best practices. The frequency of reviews should be determined based on the complexity of the system and the frequency of significant incidents.
For instance, a hospital might conduct a full review annually, with smaller, more focused reviews occurring quarterly. Updates to procedures should be documented, communicated to all relevant staff, and implemented consistently across the hospital. This ensures the system remains current, efficient, and aligned with evolving needs and best practices.
Ultimate Conclusion
Source: id-integration.com
Successfully maintaining an inbound chain of custody in a hospital isn’t just about ticking boxes; it’s about building a culture of accountability and vigilance. By implementing robust documentation procedures, leveraging technology to enhance tracking, and prioritizing staff training, hospitals can create a system that safeguards patient safety and ensures compliance. Remember, it’s a continuous process of improvement, requiring regular audits, data analysis, and a commitment to adapting to evolving regulations and best practices.
The reward? Enhanced patient care, reduced risk, and peace of mind knowing that every item entering your hospital is accounted for and secure.
FAQ Compilation
What happens if a chain of custody is broken?
A broken chain of custody can lead to serious consequences, including compromised patient safety, legal repercussions, and regulatory penalties. It may render evidence inadmissible in court and damage the hospital’s reputation.
How often should chain of custody procedures be reviewed?
Procedures should be reviewed at least annually, or more frequently if there are changes in regulations, technology, or internal processes. Regular audits are crucial.
What training is essential for staff involved in chain of custody?
Training should cover proper documentation, handling procedures, security protocols, and the implications of non-compliance. Regular refresher courses are vital.
Can smaller hospitals effectively implement chain of custody systems?
Yes, even smaller hospitals can benefit from implementing a chain of custody system, albeit perhaps on a smaller scale. They can adapt best practices and leverage technology to suit their needs.