340B Federal Clinics Pharma Drug Markups
340B federal clinics pharma drug markups are a hot topic right now, sparking debate and raising eyebrows. This program, designed to help safety-net hospitals provide affordable care, has seen its share of controversy regarding how pharmaceutical companies price drugs under the 340B umbrella. We’ll delve into the complexities of this system, exploring the discounts, the markups, and the ultimate impact on patient care.
Get ready to unravel the mysteries surrounding this crucial piece of healthcare legislation!
The 340B Drug Pricing Program aims to stretch limited healthcare resources further. Eligible hospitals and clinics receive significant discounts on medications, theoretically allowing them to reinvest savings into patient care. However, the actual pricing practices of pharmaceutical companies, and how these discounts translate into savings for patients at 340B clinics, is a complex issue. We’ll explore the various pricing strategies involved, analyzing the differences between 340B and non-340B pricing, and examine the role of manufacturer rebates in the equation.
340B Program Overview
The 340B Drug Pricing Program is a vital component of the US healthcare system, designed to stretch already limited resources and improve access to medications for vulnerable populations. It achieves this by providing outpatient drug discounts to eligible healthcare organizations, allowing them to reinvest savings in patient care. Understanding its intricacies is crucial for both those involved in its operation and those who benefit from its services.The 340B program’s history traces back to the 1992 passage of the Public Health Service Act.
Recognizing the disproportionate burden of healthcare costs on safety-net hospitals serving underserved communities, Congress created this program to help these facilities offset the costs of providing care to uninsured and underinsured patients. The program’s core purpose remains consistent: to ensure that eligible providers can offer comprehensive and affordable care, particularly to vulnerable patient populations.
Eligibility Criteria for 340B Participation
Hospitals and healthcare organizations must meet specific criteria to participate in the 340B program. These criteria are rigorously defined and regularly updated by the Health Resources and Services Administration (HRSA). Key requirements generally include serving a disproportionate number of low-income patients, demonstrating a commitment to providing comprehensive healthcare services, and maintaining compliance with program regulations. Failure to meet these standards can result in program exclusion.
The application process is thorough, involving detailed documentation and verification of eligibility.
The outrageous markups on drugs at 340B federal clinics are a serious issue, impacting patient access to affordable medications. It’s a stark reminder of how healthcare disparities can arise, and it makes me think of Monali Thakur’s recent hospitalization, as reported in this article: monali thakur hospitalised after struggling to breathe how to prevent respiratory diseases. Her struggle highlights the importance of accessible, affordable healthcare, making the 340B drug pricing debate even more critical.
Types of Covered Entities Under the 340B Program
A range of healthcare organizations qualify for 340B participation. These include, but are not limited to, disproportionate share hospitals (DSHs), rural hospitals, freestanding cancer hospitals, children’s hospitals, sole community hospitals, and critical access hospitals. Additionally, certain clinics associated with these hospitals, such as those located in federally qualified health centers (FQHCs) or rural health clinics (RHCs), may also participate.
The specific requirements for each entity type are clearly Artikeld in the HRSA guidelines.
Drug Discounts Offered Through 340B
The 340B program offers substantial discounts on the average manufacturer price (AMP) of covered outpatient drugs. The exact discount varies depending on the drug manufacturer and specific medication, but discounts can be significant, often ranging from 20% to 50% or more. These discounts enable participating healthcare organizations to acquire medications at significantly reduced costs, allowing them to provide more comprehensive care and expand services to a wider range of patients.
This price reduction directly impacts the affordability and accessibility of essential medications for vulnerable populations.
Drug Markups and Pricing Strategies
The 340B Drug Pricing Program, while designed to help safety-net hospitals serve vulnerable populations, has become a focal point of debate surrounding drug pricing and manufacturer strategies. Understanding the pricing dynamics within and outside the 340B program requires examining the various strategies employed by pharmaceutical companies and the factors influencing drug costs.Pharmaceutical companies utilize a variety of pricing strategies, often influenced by factors like research and development costs, market competition, and the perceived value of the drug.
These strategies can range from cost-plus pricing (calculating price based on production costs and desired profit margin) to value-based pricing (setting price based on the drug’s clinical benefit). Patent protection and market exclusivity also play significant roles in determining a drug’s price. In a competitive market, prices tend to be lower, while drugs with strong patent protection can command higher prices.
340B Drug Pricing Compared to Non-340B Market Pricing
Drugs purchased under the 340B program are typically sold at a discounted price compared to the prices paid by hospitals and other providers outside the program. This discount is a key element of the program’s design, intended to help safety-net providers stretch their budgets. However, the extent of this discount varies significantly across different drugs and manufacturers. While some manufacturers offer substantial discounts, others offer less, leading to considerable variability in the final price paid by 340B hospitals.
This variability is a source of ongoing contention. The price difference between 340B and non-340B pricing isn’t always consistent across the board and depends on numerous factors. For example, a drug might have a significant price difference between the two markets in one instance but a minimal difference in another.
Factors Contributing to 340B Drug Markups
Several factors contribute to the observed markups, or the difference between the 340B price and the actual cost of production and distribution for the manufacturer. These factors are complex and often interconnected. One key factor is the manufacturer’s overall pricing strategy, which might involve setting a higher price in the non-340B market to offset the discounts provided under 340B.
Another is the negotiation power of the 340B covered entity, which may vary greatly based on their size and purchasing volume. Furthermore, administrative costs associated with managing the 340B program can indirectly impact pricing, though these costs are usually absorbed by the manufacturer, not passed on to the covered entity. Finally, the lack of transparency in pricing negotiations between manufacturers and 340B covered entities can make it difficult to pinpoint the exact reasons behind price differences.
Impact of Manufacturer Rebates and Discounts on 340B Pricing
Manufacturer rebates and discounts play a crucial role in shaping the final price of drugs under the 340B program. These rebates are often negotiated separately from the 340B discount and can be substantial, especially for high-cost drugs. The impact of these rebates on the overall cost to the 340B hospital can be significant, potentially reducing the net cost of the medication even after accounting for the 340B discount.
However, the complexity of these rebate structures can make it challenging to fully understand their impact on the final price paid by the 340B provider. For instance, a manufacturer might offer a large upfront discount but structure the rebate system in a way that ultimately limits the overall savings for the 340B entity. The interaction between 340B discounts and manufacturer rebates is a complex interplay that needs further examination to fully understand its effects.
Federal Clinics and 340B Participation
Source: ufl.edu
Federal clinics, part of the extensive network of healthcare facilities run by the federal government, play a significant role in providing care to underserved populations. Their participation in the 340B Drug Pricing Program allows them to acquire medications at significantly reduced prices, enabling them to stretch their budgets and serve more patients. This section delves into the specifics of federal clinic participation in the 340B program, examining examples, data on drug dispensing, cost comparisons, and the drug acquisition and dispensing flow within these facilities.
Examples of Federal Clinics Participating in the 340B Program
Several federal agencies operate clinics eligible for 340B participation. These include clinics run by the Indian Health Service (IHS), Department of Veterans Affairs (VA) healthcare facilities, and clinics within the Department of Defense (DoD) healthcare system. The specific clinics participating vary based on their eligibility criteria and enrollment within the 340B program. Precise numbers of participating clinics are not consistently published in a single, readily accessible source, however, the significant size of these agencies suggests substantial participation.
Volume of 340B Drugs Dispensed by Federal Clinics
Determining the exact volume of 340B drugs dispensed by federal clinics requires aggregating data from various agencies, a task beyond the scope of this blog post. However, given the large number of patients served by these clinics and the high prevalence of chronic conditions often requiring long-term medication, it is reasonable to assume that a substantial volume of 340B drugs is dispensed annually.
Further research into individual agency reports would be needed for precise figures. Data from the HRSA (Health Resources and Services Administration) on overall 340B program drug dispensing could provide a broader context, though it wouldn’t isolate federal clinic-specific numbers.
Comparison of Drug Acquisition Costs
The following table offers a hypothetical comparison of drug acquisition costs between a federal clinic participating in the 340B program and a non-340B provider. These figures are illustrative and based on estimations of average wholesale prices (AWP) and 340B discounts, which vary widely by drug and manufacturer. Actual costs can differ significantly.
The inflated drug prices at 340B federal clinics are a real concern, especially when considering the vulnerable senior population they often serve. Efficient, cost-effective care is crucial, and that’s why exploring solutions like those outlined in this article on reimagining collaboration in senior care a technology driven approach is so important. Ultimately, better collaboration and technology could help mitigate the impact of these 340B markups on patient access to affordable medications.
| Drug | AWP (Non-340B) | 340B Price (Federal Clinic) | Percentage Savings |
|---|---|---|---|
| Medication A | $100 | $60 | 40% |
| Medication B | $50 | $30 | 40% |
| Medication C | $200 | $100 | 50% |
| Medication D | $75 | $45 | 40% |
340B Drug Acquisition and Dispensing Flow in a Federal Clinic
The following description illustrates the flow of 340B drug acquisition and dispensing in a typical federal clinic setting.Imagine a flowchart. The process begins with the
- clinic identifying a patient’s need for a 340B-eligible medication*. This information is then
- transmitted to the pharmacy* within the clinic. The
- pharmacy verifies the patient’s eligibility* for the 340B program. If eligible, the
- pharmacy places an order with a participating 340B manufacturer or wholesaler*. The
- manufacturer/wholesaler ships the medication at the discounted 340B price* to the clinic’s pharmacy. Finally, the
- pharmacy dispenses the medication to the patient*. Each stage is marked with a small icon (e.g., a person for patient interaction, a computer for data entry, a truck for shipping) and includes data points such as estimated timeframes for each step, average number of prescriptions processed daily, and cost savings per prescription. The overall flowchart visually represents the streamlined process, highlighting the cost savings achieved through 340B participation.
Impact on Patient Care and Access
The 340B Drug Pricing Program aims to improve access to medications for vulnerable patient populations served by safety-net hospitals and clinics. However, the impact of 340B pricing on patient care and access is a complex issue with both benefits and drawbacks that require careful consideration. Understanding this impact requires examining how 340B discounts affect medication affordability and how participating facilities utilize the resulting savings.The 340B program provides participating clinics with significantly discounted drug prices, theoretically leading to increased patient access to necessary medications.
This price reduction allows clinics to offer medications at lower out-of-pocket costs for patients, potentially reducing financial barriers to treatment. However, the extent to which this translates to improved access depends on various factors, including the clinic’s own pricing strategies, patient insurance coverage, and the availability of medications.
Medication Affordability at 340B vs. Non-340B Clinics
Studies comparing medication affordability between 340B and non-340B clinics show mixed results. While some research suggests that patients at 340B clinics experience lower out-of-pocket costs, other studies find minimal differences or even higher costs in certain cases. This discrepancy may stem from variations in clinic pricing practices, insurance reimbursement rates, and the types of medications prescribed. For example, a study might show that a 340B clinic offers a specific medication at a lower cost than a comparable non-340B clinic, while another study might reveal a different outcome depending on the specific medication and patient insurance plan.
The complexity of the healthcare system and the varying factors affecting medication pricing contribute to these inconsistent findings.
Benefits and Drawbacks of 340B on Patient Care
The 340B program’s potential benefits include improved access to medications, enhanced patient services due to increased financial resources, and the ability to invest in infrastructure improvements. However, potential drawbacks include the possibility of reduced medication affordability for some patients due to clinic pricing practices, and concerns about the program’s potential to incentivize hospital expansion into areas already adequately served.
For instance, a clinic might use 340B savings to expand its services, leading to better patient care. Conversely, a clinic might prioritize revenue generation over patient affordability, leading to higher costs for patients despite the 340B discounts.
Utilization of 340B Savings for Patient Services and Infrastructure
B savings are intended to be reinvested into patient care services and infrastructure improvements. Participating facilities are expected to use these savings to expand services, improve facilities, and enhance the overall quality of care. This can include investments in staffing, equipment, technology, and patient support programs. Examples include hiring additional nurses, purchasing new medical equipment, upgrading electronic health record systems, and providing transportation assistance to patients.
However, monitoring and transparency regarding the actual utilization of these savings are crucial to ensure they are indeed used to benefit patients. A lack of transparency in how these savings are used raises concerns about potential misuse of funds. Therefore, robust oversight and accountability mechanisms are essential.
Regulatory Oversight and Compliance
The 340B Drug Pricing Program, while designed to help safety-net hospitals and clinics provide care to vulnerable populations, operates within a complex regulatory framework. Understanding this framework, including the oversight provided by HRSA and the potential consequences of non-compliance, is crucial for participating entities. This section delves into the specifics of regulatory oversight and the importance of maintaining compliance.The Health Resources and Services Administration (HRSA) plays a central role in overseeing the 340B program.
HRSA is responsible for establishing and enforcing program regulations, conducting audits, and investigating allegations of non-compliance. They work to ensure that participating entities adhere to the program’s requirements and that the program’s goals of increasing access to care for underserved populations are met. This oversight includes reviewing applications for participation, monitoring compliance through data analysis and site visits, and issuing guidance documents to clarify program requirements.
HRSA’s Role in 340B Oversight
HRSA’s responsibilities extend beyond simply approving applications. They actively monitor participating entities through various methods, including data analysis of drug purchasing and dispensing patterns. Discrepancies or unusual trends may trigger further investigation, potentially including on-site audits to verify compliance with program rules. HRSA also provides guidance and technical assistance to help entities understand and comply with regulations.
This assistance can include webinars, workshops, and one-on-one consultations to address specific challenges. Ultimately, HRSA’s goal is to ensure the integrity of the 340B program and protect the interests of both participating entities and the patients they serve.
Common 340B Compliance Issues
Several common compliance issues plague 340B participating entities. These issues often stem from a lack of understanding of complex regulations, inadequate internal controls, or unintentional errors in record-keeping. For example, inaccurate patient identification, improper drug dispensing practices (such as dispensing to ineligible patients or locations), and inadequate documentation of 340B drug usage are frequently cited violations. Another area of concern is the proper calculation and tracking of contract pharmacy sales, ensuring compliance with the requirements for off-site dispensing.
Furthermore, the complexities of managing multiple 340B covered entities within a health system can lead to compliance challenges.
The 340B drug pricing program for federal clinics is constantly debated, with concerns about potential markups. It’s interesting to consider how this impacts large-scale primary care initiatives like the ones offered by Humana, as seen in their partnership with Walmart detailed on this site: humana centerwell primary care centers walmart. Understanding their pricing models and whether they participate in 340B is crucial for assessing the overall impact on patient costs.
Penalties for 340B Non-Compliance
Non-compliance with 340B regulations can result in a range of penalties, from financial penalties and corrective action plans to debarment from the program. The severity of the penalty depends on the nature and extent of the violation. Minor infractions may result in warnings or requirements for corrective action, while more serious violations can lead to significant financial penalties.
In extreme cases, HRSA can terminate a covered entity’s participation in the 340B program, effectively cutting off access to discounted drug pricing. The loss of 340B discounts can have a significant financial impact on safety-net hospitals and clinics, potentially impacting their ability to provide essential services to vulnerable patients. Furthermore, reputational damage resulting from public disclosure of non-compliance can further harm the organization.
Successful 340B Compliance Strategies
Successful 340B compliance hinges on proactive strategies. This includes establishing a robust compliance program with clearly defined policies and procedures, ongoing employee training, and regular internal audits. Implementing a dedicated 340B compliance officer or team is crucial for managing the complexities of the program. Effective use of technology, such as 340B-specific software, can assist in tracking drug usage, verifying patient eligibility, and generating accurate reports.
Regular review and updates of policies and procedures are essential to adapt to evolving regulations and best practices. Finally, seeking guidance and support from HRSA and other compliance experts can prove invaluable in maintaining compliance and avoiding potential penalties. For example, a large hospital system might establish a dedicated 340B compliance department with staff dedicated to training, auditing, and reporting, using specialized software to track all aspects of their 340B participation.
A smaller clinic might contract with a 340B compliance consulting firm to conduct regular audits and provide guidance on best practices.
Future of the 340B Program: 340b Federal Clinics Pharma Drug Markups

Source: slideplayer.com
The 340B Drug Pricing Program, while vital for safety-net hospitals and clinics, faces an uncertain future. Ongoing debates and potential policy shifts could significantly alter its impact on patient care and the healthcare landscape. Understanding these potential changes and their implications is crucial for stakeholders across the healthcare system.
The 340B program’s future hinges on several key factors, including evolving political priorities, ongoing legal challenges, and the persistent need to balance the program’s goals with the financial interests of pharmaceutical manufacturers and other healthcare providers. The program’s effectiveness in achieving its intended goals is constantly being scrutinized, leading to a dynamic environment ripe for reform and potential disruption.
Potential Policy Changes and Their Implications
Potential policy changes could range from minor adjustments to the program’s regulations to complete overhaul. For instance, stricter enforcement of existing rules regarding manufacturer participation and compliance could significantly impact drug availability for 340B hospitals. Conversely, expansion of the program to include additional provider types could increase access for underserved populations but might also strain the program’s resources and raise concerns about drug pricing.
A shift in reimbursement rates for 340B-acquired drugs could alter the financial stability of participating facilities, potentially impacting their ability to provide care. The potential impact of any of these changes needs careful consideration.
Ongoing Debates and Controversies Surrounding 340B Drug Pricing
The core controversy surrounding 340B revolves around drug pricing and the alleged practice of “double dipping,” where covered entities are accused of purchasing drugs at a discounted 340B price and then charging patients significantly more. This practice, while potentially illegal and unethical, is a complex issue with varying interpretations and legal challenges. Manufacturers have argued that the program’s current structure creates unfair financial burdens on them, leading to legal battles and efforts to limit their participation.
These disputes have resulted in numerous court cases and legislative efforts to amend the program. The outcome of these debates will significantly impact the program’s long-term viability.
Areas for Improvement in the 340B Program
Improving the 340B program requires a multifaceted approach. Enhanced transparency in drug pricing and purchasing practices would help address concerns about potential abuse. Strengthening oversight and enforcement mechanisms is crucial to ensure compliance and prevent fraud. Streamlining the program’s administrative processes would reduce the burden on participating providers. Lastly, improved data collection and analysis could provide a clearer picture of the program’s effectiveness and identify areas for targeted improvement.
Potential Future Directions for the 340B Program, 340b federal clinics pharma drug markups
The future of the 340B program presents both challenges and opportunities. Careful consideration of the following factors will be crucial in shaping its trajectory:
- Increased Transparency and Accountability: Implementing stricter reporting requirements and independent audits to ensure compliance and prevent potential abuses.
- Enhanced Oversight and Enforcement: Strengthening the Health Resources and Services Administration (HRSA)’s enforcement capabilities to address non-compliance and fraud.
- Expansion of Covered Entities: Carefully evaluating the potential benefits and challenges of expanding the program to include new types of providers, ensuring that expansion does not negatively impact the program’s financial stability.
- Improved Data Collection and Analysis: Gathering more comprehensive data on drug pricing, patient access, and program costs to inform future policy decisions and program improvements.
- Negotiation of Drug Prices: Exploring mechanisms to negotiate lower drug prices with manufacturers, potentially mitigating the financial strain on the program and enhancing affordability for patients.
- Addressing the “Double Dipping” Controversy: Implementing clear guidelines and stricter enforcement to address concerns about potential abuse of the program and ensure fair pricing for patients.
Conclusive Thoughts
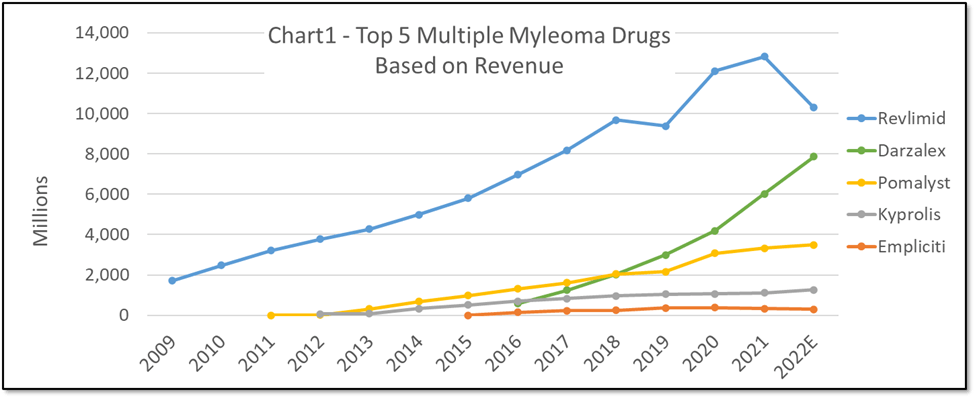
Source: pharmakb.com
Navigating the world of 340B federal clinics and pharmaceutical drug markups is a journey through complex regulations, pricing strategies, and ethical considerations. While the program aims to improve patient access to affordable medications, the realities of its implementation present challenges. Understanding the intricacies of this system – from the discounts offered to the potential for markups – is crucial for ensuring its effectiveness and fairness.
The future of 340B hinges on transparency, accountability, and a commitment to delivering quality, affordable healthcare for all.
Question & Answer Hub
What are the potential consequences for non-compliance with 340B regulations?
Non-compliance can lead to significant penalties, including financial fines, program exclusion, and even legal action. The severity of the consequences depends on the nature and extent of the violation.
How are 340B savings typically used by participating clinics?
Savings are often reinvested in various areas, such as expanding patient services, improving infrastructure, upgrading equipment, or supporting staff training programs, all aimed at enhancing patient care.
Who is eligible to participate in the 340B program?
Eligibility is primarily based on serving a significant number of low-income patients and meeting specific criteria defined by HRSA. This includes designated hospitals, clinics, and other healthcare providers.
Are all drugs covered under the 340B program?
No, not all drugs are covered. The list of covered medications can change, and some manufacturers may opt out of the program or have limitations on the discounts they offer.