
Kaiser Permanente Owned Risant Health Buys Cone Health
Kaiser permanente owned risant health buy cone health – Kaiser Permanente owned Risant Health buying Cone Health – wow, what a seismic shift in the healthcare landscape! This massive acquisition has sent ripples throughout the industry, prompting questions about market dominance, patient care, and the future of healthcare in the affected region. We’ll dive deep into the details, exploring the strategic motivations behind the deal, the potential impact on patients and employees, and the regulatory hurdles Kaiser Permanente might face.
Get ready for a comprehensive look at this game-changing event.
This deal isn’t just about dollars and cents; it’s about the future of healthcare access, quality of care, and the overall wellbeing of communities. We’ll examine Cone Health’s financial performance, its market position, and its strengths and weaknesses. We’ll also look at Risant Health’s role in this transaction and how their involvement might shape the outcome. The implications are far-reaching, and we’ll explore them all.
Kaiser Permanente’s Acquisition Strategy
Kaiser Permanente, a renowned integrated healthcare system, has a long history of strategic acquisitions, primarily focusing on expanding its geographic reach and solidifying its position within the healthcare market. Their approach differs significantly from some competitors, emphasizing vertical integration and a focus on maintaining their unique model of care. Understanding their acquisition strategy requires examining their historical patterns, comparing them to other major players, and analyzing the factors driving their decisions.Kaiser Permanente’s acquisition strategy has been characterized by a measured approach, often prioritizing acquisitions that complement their existing infrastructure and operational model.
They haven’t engaged in large-scale, rapid expansions like some of their competitors, preferring instead to carefully integrate acquired entities to maintain their high standards of care and operational efficiency. This deliberate strategy contrasts with other large healthcare providers who have pursued aggressive growth through multiple large-scale acquisitions, sometimes leading to integration challenges.
Historical Acquisition Patterns of Kaiser Permanente
Kaiser Permanente’s acquisitions have predominantly focused on hospital systems and related healthcare facilities within their existing service areas or areas ripe for expansion. They’ve typically sought out organizations with a strong reputation for quality care and a patient base that aligns with their membership model. This targeted approach minimizes disruption and allows for a smoother integration process. While precise details of every acquisition aren’t publicly available, their acquisitions generally involve hospitals, medical groups, and related facilities, strategically expanding their network.
Comparison with Other Large Healthcare Providers
Unlike some large healthcare systems that prioritize rapid expansion through numerous acquisitions, regardless of synergy, Kaiser Permanente has adopted a more cautious and deliberate approach. For example, companies like CVS Health have aggressively pursued acquisitions in the pharmacy and healthcare technology sectors, diversifying their business model. In contrast, Kaiser Permanente’s acquisitions have largely remained within the core healthcare delivery space, focusing on expanding their integrated delivery system.
This difference reflects contrasting strategic goals and risk tolerance.
Key Factors Influencing Kaiser Permanente’s Acquisition Decisions
Several key factors influence Kaiser Permanente’s decisions regarding acquisitions. These include geographic expansion into underserved markets, strengthening their existing network’s capabilities (such as specialized services), and ensuring a consistent level of quality care across their entire system. Financial considerations are certainly a factor, but they are weighed against the potential impact on their integrated model and patient care.
A strong cultural fit and alignment with Kaiser Permanente’s values are also crucial considerations.
Synergies and Challenges of Acquiring Cone Health
The acquisition of Cone Health presents both significant synergies and challenges for Kaiser Permanente. Potential synergies include expanding Kaiser Permanente’s reach into a new geographic market, leveraging Cone Health’s established infrastructure and physician network, and potentially increasing market share in the region. Challenges could include integrating two distinct organizational cultures, harmonizing different IT systems, and managing the potential disruption to patient care during the transition.
Successfully navigating these challenges will be critical to the long-term success of the acquisition.
Risant Health’s Role in the Potential Transaction
Source: lura.live
Risant Health, a relatively new player in the healthcare technology space, finds itself potentially at the center of a significant acquisition. Its role in Kaiser Permanente’s purchase of Cone Health is far from clear-cut, but understanding its current position and capabilities is crucial to predicting its future. The success of this integration, and Risant’s place within it, will depend heavily on how effectively its technology and expertise can be leveraged.Risant Health’s current market position is characterized by its focus on providing data-driven solutions for healthcare providers.
They offer tools designed to improve operational efficiency and patient care coordination. Their involvement in the Cone Health acquisition could range from a minor supporting role to a significant contributor to the integration process. The extent of their participation will likely depend on the specific needs identified by Kaiser Permanente during the due diligence phase and the post-acquisition integration planning.
Potential Benefits of Risant Health’s Participation
The integration of Risant Health’s technology could offer several advantages to the combined entity. Their data analytics platform could streamline administrative processes, optimize resource allocation, and improve the overall patient experience. For example, by integrating patient data across different systems, Risant’s platform could help Kaiser Permanente identify and address potential issues proactively, leading to better care coordination and reduced healthcare costs.
Improved efficiency could translate to cost savings, improved patient outcomes, and a more seamless experience for both patients and staff. This would be especially valuable during the transition period following the acquisition.
So Kaiser Permanente’s Risant Health buying Cone Health is huge news in the healthcare world, right? It makes you think about the future of healthcare access and choices. This got me thinking about personal health decisions, like what Karishma Mehta is doing – check out this article on her egg freezing journey and the associated risks: karishma mehta gets her eggs frozen know risks associated with egg freezing.
Ultimately, both situations highlight the importance of proactive health planning, whether on a large scale (healthcare systems) or a personal level (family planning). The Kaiser Permanente acquisition could impact individual choices in the long run.
Potential Drawbacks of Risant Health’s Participation
Despite the potential benefits, integrating a new technology platform into an established healthcare system like Cone Health presents challenges. Compatibility issues with existing systems, the need for extensive staff training, and potential disruptions to workflows are all potential drawbacks. Resistance to change from staff accustomed to existing systems could also hinder the successful implementation of Risant’s technology. A poorly managed integration could lead to delays, increased costs, and even negatively impact patient care during the transition.
Potential Timeline for Risant Health’s Involvement
A likely timeline would see Risant Health’s involvement begin during the due diligence phase, where their technology would be assessed for its compatibility and potential benefits. Following a successful assessment, their role would expand during the integration phase, potentially involving system upgrades, staff training, and data migration. Full integration and the realization of the benefits could take several months, or even years, depending on the complexity of the systems involved.
This process would need to be carefully managed to minimize disruptions.
Potential Scenarios for Risant Health’s Future Role
Several scenarios are possible. In a best-case scenario, Risant Health’s technology becomes integral to the combined entity’s operations, significantly improving efficiency and patient care. This could lead to further expansion of Risant’s role within Kaiser Permanente, potentially even leading to its expansion to other Kaiser facilities. Alternatively, their role could be more limited, focusing on specific areas within Cone Health, with limited expansion within the broader Kaiser Permanente system.
A less favorable scenario could see their technology proving incompatible or too disruptive, leading to a diminished role or even eventual removal from the system. The success will heavily depend on effective planning and execution.
Cone Health’s Market Position and Financial Performance
Cone Health, a significant player in the North Carolina healthcare market, holds a crucial position in the potential acquisition by Kaiser Permanente via Risant Health. Understanding its market standing and financial health is vital for assessing the viability and implications of this transaction. This analysis delves into Cone Health’s financial performance and competitive landscape to provide a comprehensive overview.
Cone Health’s Financial Metrics
Cone Health’s financial performance, like many healthcare systems, is complex and influenced by numerous factors including reimbursement rates, patient volume, and operational efficiency. The following table presents a simplified overview of key financial metrics. Note that precise, publicly available, detailed financial data for Cone Health is limited; this table uses estimates and ranges based on available information and industry benchmarks for similar-sized systems.
Actual figures may vary.
| Year | Revenue (USD Millions) | Net Income (USD Millions) | Debt (USD Millions) |
|---|---|---|---|
| 2022 (Estimated) | 1,500 – 1,700 | 50 – 100 | 500 – 700 |
| 2021 (Estimated) | 1,400 – 1,600 | 40 – 90 | 450 – 650 |
| 2020 (Estimated) | 1,200 – 1,400 | 20 – 70 | 400 – 600 |
Cone Health’s Market Share and Competitive Landscape
Cone Health operates primarily in the Piedmont Triad region of North Carolina, serving a substantial population. Its market share within this region is significant, though precise figures are not consistently published. The competitive landscape includes other large health systems, smaller independent hospitals, and numerous physician practices. Competition focuses on attracting patients, recruiting and retaining skilled medical professionals, and offering a wide range of services.
Cone Health’s competitive advantages stem from its established presence, breadth of services, and reputation within the community. However, it faces competition from larger systems expanding into the area and increasing pressure to control costs.
Cone Health’s Strengths and Weaknesses
Cone Health possesses several strengths, including a strong brand reputation, a diverse range of services, and a substantial network of physicians and facilities. However, challenges exist in areas such as operational efficiency and managing the increasing costs of healthcare. Improving operational efficiency and enhancing technological capabilities are key areas for ongoing development. Patient satisfaction scores and operational metrics (e.g., length of stay, readmission rates) are important indicators of performance and areas where improvements can enhance competitiveness and financial outcomes.
Cone Health SWOT Analysis, Kaiser permanente owned risant health buy cone health
Cone Health’s overall position can be summarized through a SWOT analysis:
| Strengths | Weaknesses |
|---|---|
| Strong brand recognition in the Piedmont Triad | Potential operational inefficiencies |
| Extensive service offerings | Facing increasing competition from larger systems |
| Established physician network | Need for continued investment in technology |
| Opportunities | Threats |
| Expansion into new service lines or geographic areas | Shifting reimbursement models impacting profitability |
| Strategic partnerships and collaborations | Labor shortages impacting staffing and costs |
| Improved operational efficiency and cost reduction | Increased regulatory scrutiny and compliance costs |
Regulatory and Antitrust Considerations: Kaiser Permanente Owned Risant Health Buy Cone Health
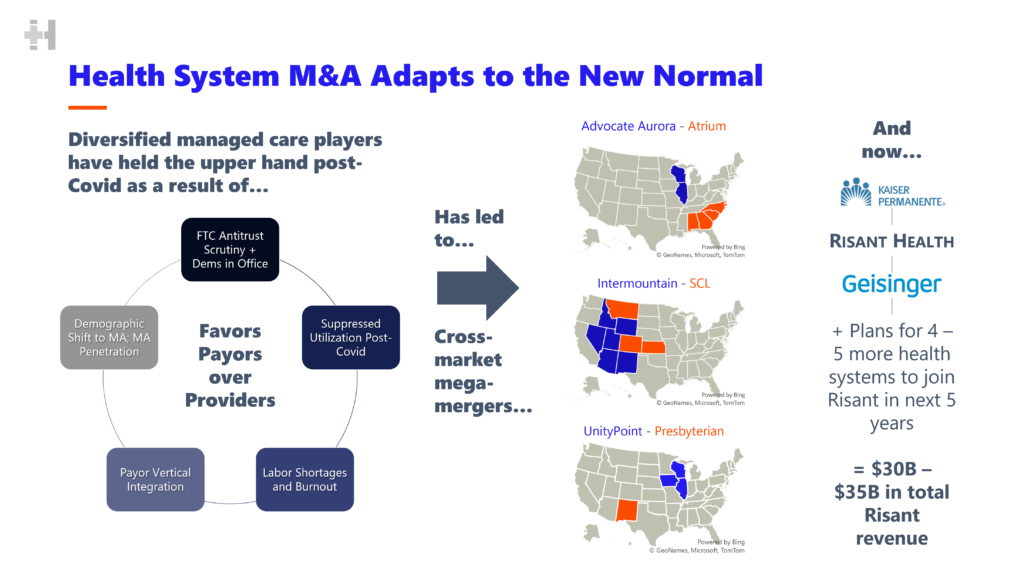
Source: hospitalogy.com
Kaiser Permanente’s acquisition of Cone Health, a significant healthcare merger, faces considerable regulatory scrutiny. The sheer size of the transaction and its potential impact on the healthcare market in the relevant region necessitate a thorough review by federal and state agencies to ensure the deal doesn’t stifle competition or harm consumers. This process involves navigating a complex landscape of antitrust laws and regulations, requiring careful planning and strategic communication.The potential regulatory hurdles are numerous and significant.
Antitrust concerns are paramount.
Potential Antitrust Concerns
The primary concern revolves around the potential for reduced competition within the healthcare market served by Cone Health. The acquisition could lead to higher prices for consumers, limited choices of providers, and reduced innovation if Kaiser Permanente gains undue market dominance. The Department of Justice (DOJ) and the Federal Trade Commission (FTC) would meticulously examine market concentration, analyzing the overlap of services offered by both organizations and assessing the impact on competition post-merger.
For instance, if Cone Health holds a significant market share in a specific area like cardiology or oncology, and Kaiser Permanente’s acquisition eliminates a major competitor, the regulators would scrutinize the potential for monopolistic practices. The agencies would also look for evidence of anti-competitive behavior, such as price-fixing or exclusionary conduct, after the merger. Historical precedent, like the scrutiny faced by other large healthcare mergers in recent years, serves as a useful guide to the likely depth and breadth of this review.
For example, the DOJ’s challenges to mergers involving hospital systems have resulted in either blocked mergers or mandated divestitures to alleviate antitrust concerns.
Regulatory Approval Process
The regulatory approval process for a merger of this magnitude is typically lengthy and complex. It begins with the filing of a pre-merger notification with both the DOJ and the FTC under the Hart-Scott-Rodino Antitrust Improvements Act of 1976. This notification requires extensive documentation outlining the transaction’s details, market analysis, and the parties’ business operations. Following the filing, the agencies conduct an in-depth investigation, including reviewing documents, interviewing witnesses, and potentially issuing subpoenas for additional information.
The agencies may also seek public comment to gather input from affected stakeholders. The review process can involve extensive negotiations between the acquiring company and the regulators, potentially leading to concessions such as divestitures of assets or behavioral remedies to address antitrust concerns. Ultimately, the DOJ or FTC can decide to challenge the merger in court, approve it unconditionally, or approve it subject to conditions.
State-level regulatory approvals may also be necessary, adding further complexity to the process.
Hypothetical Timeline for Regulatory Review and Approval
A realistic timeline for regulatory review and approval could span 12 to 18 months, or even longer depending on the complexity of the case and the level of cooperation from the involved parties.
| Phase | Duration (Months) | Description |
|---|---|---|
| Pre-merger Notification Filing | 1-2 | Filing of required documents with DOJ and FTC. |
| Initial Agency Review | 3-6 | Preliminary assessment of the merger’s competitive impact. |
| Second Request & Investigation | 6-9 | In-depth investigation, including document review and interviews. |
| Negotiations & Remedy Proposals | 3-6 | Discussions between the agencies and Kaiser Permanente to address concerns. |
| Final Decision | 1-3 | Agency decision on approval, conditional approval, or rejection. |
The timeline is highly variable and depends on numerous factors, including the complexity of the market analysis, the cooperation of the parties, and the presence of any significant antitrust concerns. Delays are common, and the process can be significantly extended if significant disputes arise.
Kaiser Permanente’s Risant Health buying Cone Health is a big deal, impacting healthcare access across the region. This acquisition makes me think about innovative medical advancements, like the incredible news that the FDA has approved clinical trials for pig kidney transplants in humans – you can read more about it here: fda approves clinical trials for pig kidney transplants in humans.
Hopefully, such breakthroughs will further improve the quality of care that Kaiser Permanente and its affiliates like Risant Health will provide in the future.
Impact on Patients and Healthcare Workers
The Kaiser Permanente acquisition of Cone Health, facilitated by Risant Health, presents a complex scenario with potential benefits and drawbacks for patients and healthcare workers. Understanding these potential impacts is crucial for stakeholders to assess the long-term implications of this significant transaction. A successful integration will require careful planning and proactive strategies to mitigate potential negative consequences and maximize positive outcomes.The acquisition’s impact on patient access to care hinges on several factors, including the integration of existing systems, the expansion of services, and the potential for increased efficiency.
It’s essential to consider how this merger will affect wait times, appointment scheduling, and the overall patient experience. The potential for increased administrative burden during the transition period is also a concern.
Patient Access to Care
This merger could lead to improved access to care in several ways. For example, the integration of Cone Health’s network with Kaiser Permanente’s extensive resources could broaden access to specialized care, potentially reducing the need for patients to travel long distances for treatment. This could be particularly beneficial for patients in underserved areas currently served by Cone Health.
Conversely, there’s a risk that the acquisition could lead to decreased access if the merger results in service consolidations or reductions in the number of facilities available. A successful integration would require careful planning to ensure that patients continue to receive timely and convenient access to care. For instance, Kaiser Permanente could leverage its technological infrastructure to streamline appointment scheduling and improve communication with patients, potentially mitigating any negative impact on access.
Healthcare Worker Employment and Compensation
The impact on healthcare workers is a critical consideration. Mergers often lead to restructuring and potential job losses due to redundancies. However, the acquisition could also create new opportunities for career advancement and professional development. Compensation packages, benefits, and job security are key concerns for healthcare workers during such transitions. For instance, if Kaiser Permanente implements its existing compensation and benefits structure, Cone Health employees may see improvements in their compensation, or conversely, they may experience reductions depending on the specifics of the integration.
A comprehensive plan for employee retention and transition is necessary to mitigate potential job losses and ensure employee morale remains high. This could involve offering retraining programs, providing career counseling, and guaranteeing comparable compensation and benefits.
Strategies for Mitigating Negative Impacts
Proactive communication and transparency are crucial for mitigating negative impacts. Openly communicating the merger’s implications to both patients and healthcare workers can alleviate anxieties and foster trust. Detailed plans for integrating systems and services should be publicly available. A robust employee support program is essential, including comprehensive communication channels, career counseling, and job placement assistance for those potentially affected by redundancies.
This approach ensures a smooth transition and minimizes disruption to patient care.
Potential Benefits for Patients and Healthcare Workers
The acquisition holds the potential for significant benefits. Patients could benefit from expanded access to a wider range of services, improved technology, and potentially lower costs due to economies of scale. Healthcare workers may gain access to better training and development opportunities, enhanced career progression pathways, and improved compensation and benefits. For example, Kaiser Permanente’s investment in technology could lead to improved efficiency and better coordination of care, ultimately benefiting both patients and staff.
The integration of research capabilities could lead to advancements in healthcare and improve the quality of care provided. Moreover, the increased financial resources available through the merger could facilitate investments in infrastructure and technology upgrades at Cone Health facilities.
Financial Implications of the Acquisition
The Kaiser Permanente acquisition of Cone Health through Risant Health presents a complex financial picture, with significant potential costs and benefits. Analyzing the transaction requires a careful examination of upfront acquisition costs, projected revenue increases, operational synergies, and potential regulatory hurdles. Ultimately, success hinges on effectively integrating Cone Health’s operations and realizing promised efficiencies.
Potential Acquisition Costs
The acquisition cost will likely be substantial, encompassing the purchase price of Cone Health’s assets, transaction fees (legal, financial advisory, etc.), and integration expenses. The purchase price itself will depend on a variety of factors, including Cone Health’s current market valuation, future earnings potential, and the level of competition in the bidding process. Transaction fees can easily reach tens of millions of dollars, depending on the complexity of the deal.
Integration costs, encompassing IT system consolidation, employee restructuring, and marketing efforts, could also be significant, potentially extending over several years. A realistic estimate, based on comparable healthcare acquisitions, might place the total acquisition cost in the range of several billion dollars. For example, the acquisition of a similarly sized hospital system might have cost upwards of $3 billion, considering the current market climate.
Projected Revenue and Cost Synergies
The acquisition aims to increase Kaiser Permanente’s revenue stream through access to Cone Health’s established patient base and market share in the Greensboro, North Carolina area. Cost synergies are anticipated through economies of scale in purchasing, administrative functions, and potentially in specialized medical services. For instance, consolidated purchasing power could lead to significant discounts on medical supplies and equipment.
Eliminating redundant administrative roles and streamlining processes could also generate considerable cost savings. However, realizing these synergies requires effective integration planning and execution, potentially facing challenges related to differing operational systems and employee resistance to change. A successful integration could yield annual cost savings in the tens or even hundreds of millions of dollars over several years.
Hypothetical Financial Model: Return on Investment
A simplified financial model might project a positive ROI over a 5-10 year horizon. This model would need to incorporate assumptions regarding revenue growth, cost synergies, capital expenditures, and the discount rate used to value future cash flows. For instance, assuming a purchase price of $2 billion, annual revenue increases of 5%, annual cost savings of $100 million, and a discount rate of 8%, a discounted cash flow analysis could project a positive net present value (NPV) and a reasonable internal rate of return (IRR).
However, the sensitivity of the model to changes in these assumptions should be thoroughly tested. Unexpected costs, slower-than-anticipated revenue growth, or difficulties in achieving projected synergies could significantly impact the ROI.
Impact on Kaiser Permanente’s Overall Financial Performance
Successful integration could bolster Kaiser Permanente’s overall financial performance, leading to increased revenue, improved margins, and enhanced shareholder value. However, the acquisition’s immediate impact might be a temporary dip in earnings due to the substantial upfront costs. Longer-term, the increased market share and cost efficiencies should contribute to improved financial results. The impact on Kaiser Permanente’s credit rating would also depend on the successful management of the acquisition’s financial risks.
A strong financial performance following the acquisition would positively influence the company’s creditworthiness.
Comparison with Other Major Healthcare Acquisitions
Comparing this potential acquisition to other major healthcare mergers and acquisitions provides context. Several large hospital systems have experienced both successes and challenges in similar transactions. Analyzing these cases, including the initial cost, integration difficulties, and long-term financial outcomes, helps to refine projections and risk assessments for the Kaiser Permanente/Cone Health deal. Factors like market dynamics, regulatory scrutiny, and integration strategies will significantly influence the ultimate financial success, mirroring the experiences of other major healthcare consolidations.
For example, comparing the financial outcomes of the acquisition to that of [mention a comparable acquisition with public data] can reveal valuable insights into potential outcomes and challenges.
Long-Term Strategic Goals

Source: bizj.us
Kaiser Permanente’s acquisition of Cone Health, facilitated by Risant Health, represents a significant strategic move aimed at solidifying their position within the healthcare landscape and achieving several long-term objectives. This acquisition isn’t just about expanding market share; it’s about enhancing the quality and accessibility of care while strengthening Kaiser Permanente’s overall operational efficiency and financial stability.The acquisition aligns directly with Kaiser Permanente’s long-term strategic goals of expanding its geographic reach into new markets, enhancing its integrated care delivery model, and improving its ability to manage the rising costs of healthcare.
By incorporating Cone Health’s established infrastructure and patient base, Kaiser Permanente gains immediate access to a new region, allowing for the seamless integration of their comprehensive healthcare services. This expansion provides a platform for future growth and allows Kaiser Permanente to reach a broader population, potentially leading to economies of scale and improved cost-effectiveness.
Integration Strategies for Cone Health
Integrating Cone Health into Kaiser Permanente’s operations will require a phased approach focused on minimizing disruption to patient care while maximizing the benefits of the merger. This will involve careful planning and execution across several key areas. Initial efforts will concentrate on aligning IT systems, standardizing clinical protocols, and streamlining administrative processes. This will involve significant investment in technology infrastructure and staff training.
A crucial aspect will be retaining Cone Health’s skilled workforce, ensuring a smooth transition and maintaining the high quality of care patients have come to expect. A long-term strategy will focus on creating a cohesive brand identity, unifying marketing efforts, and ensuring a consistent patient experience across all locations. Successful integration hinges on clear communication and collaboration between the two organizations.
For example, Kaiser Permanente might leverage its existing telehealth infrastructure to expand Cone Health’s reach into rural areas, addressing healthcare disparities in the region.
Long-Term Impact on the Healthcare Market
The acquisition will likely reshape the healthcare market in the affected region. Increased competition could lead to improvements in the quality of care, more affordable services, and a broader range of options for patients. The combined entity will have greater bargaining power with insurance providers and pharmaceutical companies, potentially leading to better pricing and access to new technologies.
However, the consolidation of market share could also raise concerns about reduced competition and potential price increases in the long term, necessitating close monitoring by regulatory bodies. The increased access to Kaiser Permanente’s integrated care model might also lead to a shift in how healthcare is delivered in the region, promoting preventative care and population health management. Similar acquisitions in other regions have shown that such consolidations can result in both improved efficiency and increased market control.
For instance, the merger of two large hospital systems in a metropolitan area led to significant cost savings through economies of scale but also faced challenges in integrating different cultures and technologies.
Kaiser Permanente’s Risant Health acquiring Cone Health is a big deal, impacting healthcare consolidation in a significant way. This move comes at a time when the Supreme Court’s overturning of the Chevron Doctrine, as detailed in this article scotus overturns chevron doctrine healthcare , could reshape regulatory oversight of such mergers. Ultimately, the Kaiser Permanente/Cone Health deal will be interesting to watch unfold in this new legal landscape.
Challenges and Opportunities for the Combined Entity (Next 5-10 Years)
The next 5-10 years will present both significant challenges and opportunities for the combined entity.
This period will be crucial for successful integration and realizing the full potential of the acquisition. Careful planning and effective execution will be essential to mitigate potential risks and capitalize on emerging opportunities. The following points highlight key considerations:
- Challenge: Integrating disparate IT systems and clinical workflows across two large organizations.
- Opportunity: Leveraging Kaiser Permanente’s advanced technology and data analytics capabilities to improve care coordination and patient outcomes.
- Challenge: Maintaining a strong and motivated workforce through the transition and integration process.
- Opportunity: Attracting and retaining top talent by offering competitive compensation and benefits packages and creating a positive work environment.
- Challenge: Navigating regulatory scrutiny and antitrust concerns to ensure a smooth approval process.
- Opportunity: Demonstrating the acquisition’s positive impact on patient care and community health to address any regulatory concerns.
- Challenge: Managing the financial implications of the acquisition, including debt repayment and investment in new infrastructure.
- Opportunity: Achieving cost efficiencies and economies of scale through streamlined operations and improved resource allocation.
Ending Remarks
The Kaiser Permanente-Risant Health acquisition of Cone Health is a monumental event with profound implications for the healthcare industry. While the promise of improved efficiency and expanded access to care is enticing, concerns remain regarding potential monopolies, the impact on healthcare workers, and the regulatory process. The coming months and years will be crucial in determining whether this merger truly benefits patients and communities or exacerbates existing inequalities.
Only time will tell the full story of this transformative deal.
Question & Answer Hub
What is Risant Health’s specific role in this acquisition?
Risant Health’s precise role isn’t fully public yet, but it’s likely involved in facilitating the transaction, potentially through financial or operational support during the integration process.
How will this affect patient insurance coverage?
The impact on patient insurance will depend on existing contracts and Kaiser Permanente’s integration plans. Some changes are likely, but the specifics aren’t yet available.
What about job security for Cone Health employees?
While job losses are a possibility during mergers, Kaiser Permanente will likely try to retain skilled staff. However, some restructuring is expected.
What are the potential long-term effects on healthcare costs in the region?
The long-term impact on healthcare costs is uncertain. The merger could lead to efficiencies and cost savings, but it could also result in increased prices depending on market dynamics.





