88 Percent Healthcare Organizations Report Cyberattack Ponemon Institute
88 percent healthcare organizations report cyberattack ponemon institute – 88 percent healthcare organizations report cyberattack, according to the Ponemon Institute. This staggering statistic highlights a critical vulnerability in an industry entrusted with our most sensitive personal information. The report details a widespread problem, revealing the types of attacks, their devastating consequences, and the urgent need for improved cybersecurity measures. This isn’t just about numbers; it’s about the real-world impact on patient care, financial stability, and public trust.
The Ponemon Institute’s research meticulously examines the scope of the problem, delving into the specific types of cyberattacks experienced, the financial and operational ramifications, and the legal implications of data breaches. By understanding the vulnerabilities and exploring effective mitigation strategies, we can begin to build a more resilient healthcare ecosystem. The report serves as a crucial wake-up call, urging healthcare organizations to prioritize cybersecurity and invest in robust defenses.
The Scope of the Ponemon Institute Report
The Ponemon Institute’s report on cybersecurity in the healthcare sector paints a stark picture: a significant majority of healthcare organizations have experienced a cyberattack. The frequently cited 88% figure highlights the pervasive nature of this threat and underscores the urgent need for improved cybersecurity measures within the industry. This report delves deeper into the methodology, scope, and findings of this impactful research.The report’s methodology is crucial to understanding the validity of the 88% statistic.
While the precise details of their methodology might vary from study to study (as Ponemon Institute publishes multiple reports on this topic), it generally involves surveying a large sample of healthcare organizations. This typically includes questionnaires, interviews, and potentially analysis of incident response data. The selection process aims for a representative sample, ensuring that the findings can be reasonably extrapolated to the broader healthcare landscape.
This involves careful consideration of factors like organization size, type, and geographical location to avoid bias. The resulting data is then analyzed to determine the prevalence of cyberattacks and related security challenges.
Types of Healthcare Organizations Included in the Study
The Ponemon Institute’s reports usually encompass a diverse range of healthcare organizations. This typically includes hospitals of varying sizes (from small community hospitals to large academic medical centers), clinics (both large multi-specialty clinics and smaller, single-specialty practices), physician practices, and potentially other healthcare-related entities such as health insurance providers and pharmaceutical companies. The specific inclusion criteria might vary depending on the research objectives of each individual study.
The broad inclusion of various organization types is essential to provide a comprehensive view of the cybersecurity challenges faced across the healthcare sector.
Geographical Distribution of Surveyed Organizations, 88 percent healthcare organizations report cyberattack ponemon institute
The geographical scope of Ponemon Institute’s research often extends across multiple countries. While the exact regions covered can change between studies, the reports usually aim to capture a global perspective on cybersecurity in healthcare. This helps to identify common vulnerabilities and trends across different healthcare systems and regulatory environments. The inclusion of diverse geographical locations enhances the generalizability of the findings, offering insights applicable beyond specific regions.
However, it’s important to note that the weighting of different regions within the sample might influence the overall results. For instance, a higher proportion of organizations from a specific region might lead to a stronger representation of the cybersecurity challenges prevalent in that area.
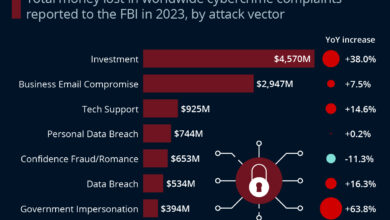
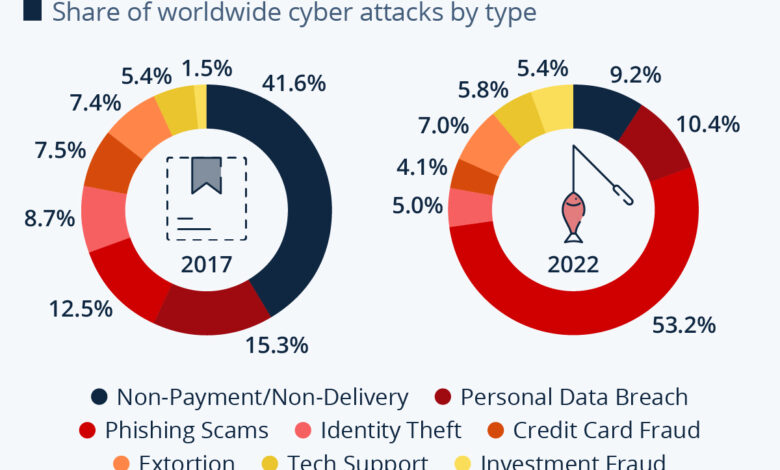
Types of Cyberattacks Experienced
Source: nih.gov
The Ponemon Institute’s report highlights a grim reality: a significant percentage of healthcare organizations face cyberattacks. Understanding the types of attacks, their frequency, impact, and mitigation strategies is crucial for bolstering cybersecurity defenses within this vulnerable sector. This section delves into the specific threats reported, providing examples and practical strategies for improvement.
The following table summarizes the most prevalent cyberattack types reported by the 88% of healthcare organizations included in the Ponemon Institute study. Note that the frequency and impact are generalizations based on the report’s findings and may vary depending on the specific organization and the nature of the attack.
| Attack Type | Frequency | Impact | Mitigation Strategies |
|---|---|---|---|
| Ransomware | High | Data loss, operational disruption, financial losses, reputational damage, potential HIPAA violations | Regular data backups, strong endpoint security, employee training on phishing and social engineering, multi-factor authentication, robust incident response plan |
| Phishing and Social Engineering | Very High | Data breaches, malware infections, compromised credentials, financial losses | Security awareness training for employees, robust email filtering, multi-factor authentication, regular security audits |
| Malware Infections (including viruses, worms, Trojans) | High | Data breaches, system disruptions, data corruption, financial losses | Antivirus and anti-malware software, regular software updates, network segmentation, intrusion detection/prevention systems |
| Denial-of-Service (DoS) Attacks | Moderate | Website and system unavailability, disruption of services | Network security monitoring, DDoS mitigation solutions, robust network infrastructure |
| Insider Threats | Moderate | Data breaches, data theft, sabotage | Access control policies, background checks, employee monitoring (with appropriate legal considerations), security awareness training |
Specific Ransomware Attacks Targeting Healthcare Providers
Several high-profile ransomware attacks have crippled healthcare providers, highlighting the severity of this threat. The WannaCry ransomware attack in 2017, for instance, affected numerous hospitals globally, disrupting patient care and causing significant financial losses. Another example is the Ryuk ransomware, known for targeting critical infrastructure, including hospitals, leading to delayed surgeries and compromised patient data. These attacks demonstrate the devastating consequences of successful ransomware deployments in the healthcare sector.
The Role of Phishing and Social Engineering
Phishing and social engineering attacks remain a significant entry point for many cyberattacks against healthcare organizations. Attackers often employ sophisticated techniques, such as spear phishing (highly targeted emails) and pretexting (creating false scenarios to gain trust), to manipulate employees into revealing sensitive information or downloading malicious software. The human element remains a crucial vulnerability, emphasizing the need for robust security awareness training and education programs.
The Ponemon Institute’s alarming statistic – 88 percent of healthcare organizations reporting cyberattacks – really hits home when you consider the financial impact. Check out this article on elevance health earnings, their Q1 changes, and how a cyberattack affected their Medicaid and Medicare Advantage programs , it’s a stark reminder of how widespread and costly these breaches are.
The 88 percent figure underscores the urgent need for better cybersecurity practices across the entire healthcare sector.
Malware and Other Malicious Software
Malware, encompassing viruses, worms, Trojans, and other malicious code, plays a central role in many healthcare cyberattacks. These malicious programs can steal data, disrupt operations, and encrypt critical systems, leading to significant financial and operational losses. The sophistication of malware is constantly evolving, requiring organizations to employ comprehensive security measures, including robust antivirus and anti-malware solutions, regular software updates, and network segmentation to minimize the risk of infection.
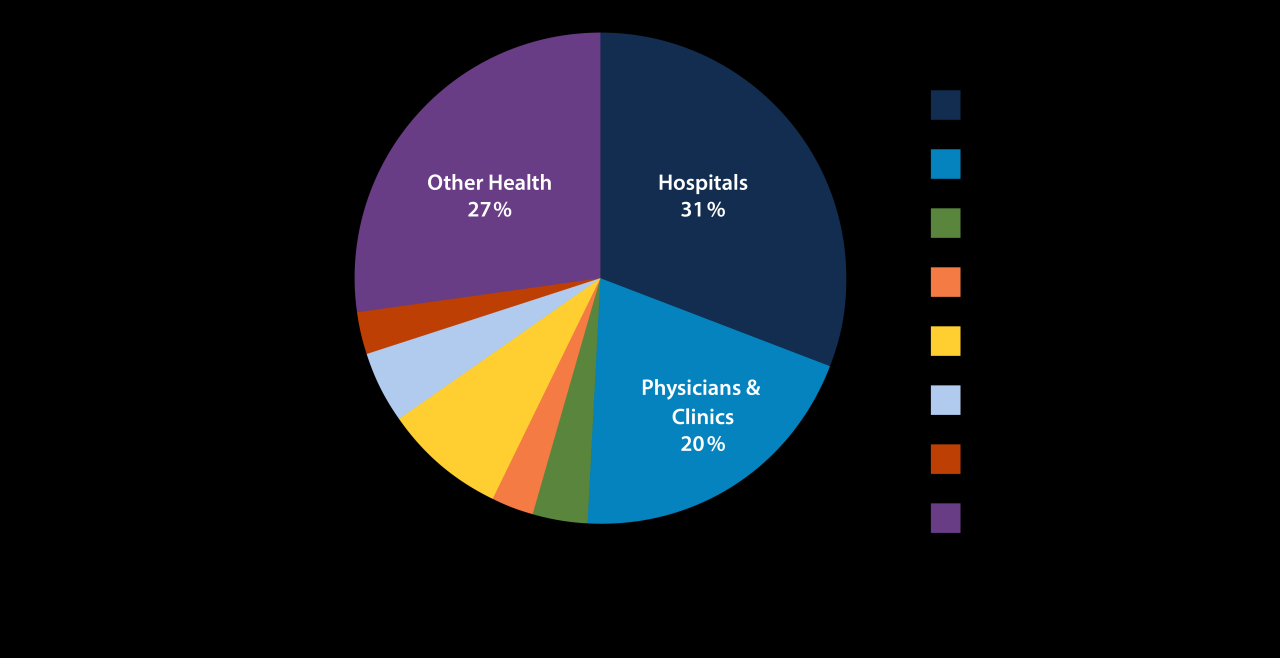
Impact of Cyberattacks on Healthcare Organizations
The staggering 88% figure from the Ponemon Institute highlighting healthcare organizations experiencing cyberattacks underscores a critical issue: the devastating impact these attacks have on various aspects of healthcare operations. Beyond the immediate disruption, these incidents ripple outwards, causing significant financial losses, operational chaos, reputational damage, and severe compromises to patient data privacy. Understanding the full scope of this damage is crucial for developing effective preventative and responsive measures.
Financial Consequences of Cyberattacks
Cyberattacks against healthcare providers inflict substantial financial burdens. Ransom payments, a common tactic used by malicious actors, can reach millions of dollars, forcing organizations to choose between paying criminals or facing prolonged system outages. Beyond ransom demands, the costs associated with incident response are considerable. This includes engaging cybersecurity experts, forensic investigators, legal counsel, and public relations firms to manage the crisis, investigate the breach, and mitigate its impact.
Legal fees, particularly in cases involving regulatory violations like HIPAA non-compliance, can quickly escalate the financial strain. For example, the 2015 Anthem data breach, which exposed the personal information of nearly 80 million individuals, resulted in hundreds of millions of dollars in costs related to investigation, remediation, and legal settlements.
Operational Disruptions Caused by Cyberattacks
The operational disruption caused by cyberattacks can be equally damaging. System downtime, a frequent consequence of ransomware attacks or data breaches, severely impacts patient care. Imagine a hospital’s electronic health record (EHR) system becoming inaccessible – appointments are missed, surgeries are delayed, and critical patient information is unavailable. This leads to decreased efficiency, increased workload for staff, and, most importantly, potential harm to patients.
Furthermore, the recovery process can be lengthy and complex, requiring significant time and resources to restore systems and data, causing further disruption and financial losses. The disruption extends beyond immediate patient care; administrative functions, billing systems, and research activities can all be severely affected, hindering the overall functioning of the organization.
Reputational Damage Following Cyberattacks
The reputational damage suffered by healthcare organizations after a cyberattack can be long-lasting. Public disclosure of a data breach, particularly one involving sensitive patient information, can severely erode public trust. Patients may lose confidence in the organization’s ability to protect their data, leading to a decline in patient volume and negative publicity. This damage can impact recruitment and retention of staff, as potential employees may be hesitant to join an organization with a history of security breaches.
The long-term effects on the organization’s brand and reputation can be significant, requiring substantial investment in rebuilding trust and restoring confidence. The 2017 Equifax data breach, although not in healthcare, serves as a powerful example of how reputational damage can translate into long-term financial and operational consequences.
With a staggering 88 percent of healthcare organizations reporting cyberattacks, according to the Ponemon Institute, the news about hshs prevea closing Wisconsin hospitals and health centers raises serious concerns. This closure, however temporary, highlights the vulnerability of even large healthcare systems, underscoring the urgent need for robust cybersecurity measures to protect patient data in the face of increasingly sophisticated attacks.
Impact on Patient Data Privacy and Security
The unauthorized access and potential disclosure of sensitive patient data are among the most serious consequences of cyberattacks on healthcare organizations. This can lead to identity theft, medical identity theft, financial fraud, and emotional distress for affected individuals. The violation of patient privacy not only inflicts harm on individuals but also exposes the organization to significant legal and financial liabilities.
- Identity theft: Malicious actors can use stolen personal information to open fraudulent accounts, obtain loans, or file taxes illegally.
- Medical identity theft: Stolen medical information can be used to obtain fraudulent healthcare services or insurance claims.
- Financial fraud: Access to banking details can result in significant financial losses for patients.
- Emotional distress: The breach of personal and medical information can cause significant anxiety, stress, and emotional distress for affected individuals.
- Legal and regulatory penalties: Organizations face substantial fines and legal repercussions for violating HIPAA and other data privacy regulations.
- Loss of patient trust and confidence: Data breaches can severely damage an organization’s reputation and lead to a decline in patient volume.
Security Measures and Vulnerabilities
The alarming statistic that 88% of healthcare organizations have experienced a cyberattack highlights a critical vulnerability in the sector. This isn’t just about data breaches; it’s about compromising patient care, disrupting operations, and incurring significant financial losses. Understanding the security measures employed and the vulnerabilities exploited is crucial to building a more resilient healthcare cybersecurity landscape. This section delves into the common attack vectors, the range of defensive strategies, and their effectiveness in mitigating these threats.The healthcare industry faces a unique set of challenges.
The sheer volume of sensitive patient data, coupled with often outdated IT infrastructure and a workforce that may not be fully trained in cybersecurity best practices, creates a fertile ground for attackers. The consequences of a successful attack can be devastating, ranging from hefty fines for HIPAA violations to irreparable damage to a hospital’s reputation and the potential compromise of patient lives.
Commonly Exploited Vulnerabilities
Healthcare organizations are frequently targeted through several well-known vulnerabilities. Phishing emails, exploiting human error to gain access to credentials, remain a highly effective attack vector. Ransomware attacks, encrypting critical data and demanding payment for its release, continue to plague the industry. Unpatched software and outdated systems present significant weaknesses, allowing attackers to exploit known vulnerabilities. Finally, weak or easily guessed passwords contribute significantly to successful breaches.
The combination of these factors makes the healthcare sector a particularly attractive target for cybercriminals.
Cybersecurity Measures Employed by Healthcare Organizations
A range of cybersecurity measures are employed, though their effectiveness varies widely. Many organizations utilize firewalls to control network traffic and intrusion detection/prevention systems (IDS/IPS) to monitor for malicious activity. Data encryption protects sensitive information both in transit and at rest. Employee training programs aim to improve awareness of phishing scams and other social engineering tactics. Multi-factor authentication (MFA) adds an extra layer of security to access control.
Regular security audits and penetration testing help identify vulnerabilities before attackers can exploit them. However, the implementation and effectiveness of these measures are often inconsistent across the industry.
Effectiveness of Current Cybersecurity Practices
While many healthcare organizations implement various security measures, the overall effectiveness remains a concern. The 88% attack rate speaks volumes. The sheer volume of data, coupled with the complexity of healthcare IT systems and the ever-evolving tactics of cybercriminals, creates a continuous challenge. Many organizations struggle to keep pace with the latest threats and maintain adequate security posture.
Budgetary constraints, staffing shortages, and a lack of skilled cybersecurity professionals further exacerbate the problem. The reliance on legacy systems, which are often difficult and expensive to update, also contributes to persistent vulnerabilities.
Best Practices for Enhancing Cybersecurity in Healthcare
Implementing robust cybersecurity practices is paramount. A multi-layered approach is essential.
- Regular Security Assessments: Conduct frequent vulnerability scans and penetration testing to identify and address weaknesses proactively.
- Employee Security Awareness Training: Invest in comprehensive training programs to educate employees about phishing, social engineering, and other common threats.
- Strong Password Policies and Multi-Factor Authentication (MFA): Enforce strong password policies and implement MFA for all accounts accessing sensitive data.
- Data Encryption: Encrypt sensitive data both in transit and at rest to protect it from unauthorized access.
- Regular Software Updates and Patching: Maintain up-to-date software and promptly apply security patches to mitigate known vulnerabilities.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan to minimize the impact of a successful attack.
- Data Loss Prevention (DLP): Implement DLP tools to monitor and prevent sensitive data from leaving the organization’s control.
- Third-Party Risk Management: Assess and manage the cybersecurity risks posed by third-party vendors and business partners.
- Invest in Cybersecurity Expertise: Recruit and retain skilled cybersecurity professionals to manage and maintain security infrastructure and response capabilities.
Regulatory and Legal Implications
The staggering 88% of healthcare organizations experiencing cyberattacks, as reported by the Ponemon Institute, highlights a critical need to understand the complex web of regulations and legal ramifications surrounding these incidents. Failure to comply not only exposes patient data to significant risk but also invites substantial financial penalties and reputational damage. This section explores the key regulatory landscape and legal consequences impacting healthcare cybersecurity.
HIPAA and Other Relevant Regulations
The Health Insurance Portability and Accountability Act (HIPAA) is the cornerstone of healthcare data privacy and security in the United States. It mandates the implementation of administrative, physical, and technical safeguards to protect Protected Health Information (PHI). These safeguards cover a wide range of areas, including access controls, audit trails, encryption, and risk management. Beyond HIPAA, other regulations like the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR) in Europe, depending on the organization’s geographic reach and the data they handle, also play a crucial role in shaping cybersecurity practices.
Non-compliance with these regulations can result in significant penalties. For example, HIPAA violations can lead to fines ranging from $100 to $50,000 per violation, with even more substantial penalties for willful neglect.
Legal Ramifications of Data Breaches and Non-Compliance
Data breaches in healthcare settings can trigger a cascade of legal consequences. Organizations face potential lawsuits from affected individuals, class-action lawsuits, and investigations from regulatory bodies. These legal battles can be protracted and expensive, involving significant legal fees, settlements, and potential reputational damage. Beyond direct legal action, non-compliance with regulations like HIPAA can lead to hefty fines, reputational harm, and a loss of public trust, which can negatively impact the organization’s financial stability and long-term viability.
The cost of a data breach extends far beyond the immediate financial penalties, encompassing the cost of remediation, notification to affected individuals, credit monitoring services, and potential loss of business.
Role of Government Agencies in Responding to Healthcare Cyberattacks
Government agencies play a vital role in both preventing and responding to healthcare cyberattacks. In the US, the Office for Civil Rights (OCR) within the Department of Health and Human Services (HHS) enforces HIPAA regulations and investigates breaches. Other agencies like the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) also contribute to incident response and cybersecurity awareness initiatives.
These agencies provide guidance, investigate breaches, and coordinate responses to large-scale attacks. For example, CISA publishes alerts and advisories about emerging threats, while the FBI assists in investigations and law enforcement actions related to cybercrime. International cooperation is also increasingly important in addressing cross-border cyberattacks.
Improving Compliance and Reducing Risk
Healthcare organizations can proactively improve their compliance posture and reduce their risk profile through a multi-faceted approach. This includes conducting regular risk assessments to identify vulnerabilities, implementing robust security controls aligned with HIPAA and other relevant regulations, providing comprehensive employee training on cybersecurity best practices, and establishing a strong incident response plan. Regular security audits and penetration testing can identify weaknesses in the organization’s security infrastructure.
Investing in advanced security technologies such as intrusion detection systems, firewalls, and data loss prevention (DLP) tools is also crucial. Furthermore, maintaining up-to-date software and patching vulnerabilities promptly is essential to mitigate the risk of exploitation. Finally, establishing strong relationships with government agencies and cybersecurity experts can provide valuable support during incident response and in maintaining ongoing compliance.
It’s crazy to think that 88 percent of healthcare organizations reported a cyberattack, according to the Ponemon Institute. This vulnerability is especially concerning given the massive amounts of sensitive patient data involved, and the rising costs associated with treating conditions like obesity, as highlighted in this insightful KFF report on Medicare GLP-1 spending and weight loss: medicare glp1 spending weight loss kff.
The potential for data breaches impacting these kinds of programs is a serious threat that needs immediate attention, further emphasizing the urgency of bolstering cybersecurity in healthcare.
Future Trends and Predictions
The healthcare industry’s increasing reliance on interconnected systems and the explosion of sensitive patient data make it a prime target for cybercriminals. Predicting the future of healthcare cybersecurity requires understanding current trends and extrapolating from them, recognizing the dynamic nature of the threat landscape. This means anticipating not only the evolution of existing attack vectors but also the emergence of entirely new ones.The evolving landscape of cyberattacks targeting the healthcare industry is characterized by increasing sophistication and a shift towards financially motivated attacks, ransomware in particular.
We’re seeing a move beyond simple data breaches to more targeted attacks aiming to disrupt operations, extort organizations, and steal intellectual property. The rise of artificial intelligence and machine learning is further complicating matters, allowing attackers to automate attacks and evade traditional security measures with greater efficiency. For example, the use of AI-powered phishing campaigns is becoming increasingly prevalent, creating more realistic and convincing attacks that are harder to detect.
Advanced Persistent Threats (APTs) and Nation-State Actors
Highly sophisticated and persistent attacks, often attributed to nation-state actors, are becoming more common. These APTs are characterized by their stealthy nature, long-term objectives, and the use of advanced techniques to maintain access to systems. The motivation behind these attacks can range from espionage to theft of intellectual property related to medical research and development. We can expect to see an increase in the complexity and duration of these types of attacks, necessitating a more proactive and robust security posture.
A real-world example would be a hypothetical scenario where a nation-state actor targets a pharmaceutical company to steal research data on a new drug, providing a significant economic and strategic advantage.
The Rise of AI-Powered Cybersecurity Tools
Technological advancements in AI and machine learning are offering new possibilities for improving healthcare cybersecurity. AI-powered security tools can analyze vast amounts of data to identify anomalies and potential threats in real-time, far exceeding the capabilities of human analysts. These tools can be used for threat detection, incident response, and vulnerability management. For example, AI algorithms can identify patterns in network traffic indicative of a malicious attack, allowing for rapid intervention and containment.
However, the use of AI in cybersecurity is a double-edged sword, as attackers are also leveraging AI to enhance their offensive capabilities. A constant arms race is expected between attackers and defenders using AI.
Proactive Cybersecurity Measures: A Critical Need
Proactive measures are no longer a luxury but a necessity. Reactive approaches, focusing solely on responding to attacks after they occur, are proving inadequate. A proactive strategy involves implementing robust security controls, conducting regular security assessments and penetration testing, and establishing strong incident response plans. Investing in employee training and awareness programs is also crucial, as human error remains a significant vulnerability.
Organizations must adopt a risk-based approach, prioritizing the protection of the most sensitive data and systems. This could involve implementing multi-factor authentication, data encryption, and regular software updates across all systems. A failure to adopt a proactive approach leaves organizations vulnerable to significant financial losses, reputational damage, and legal repercussions.
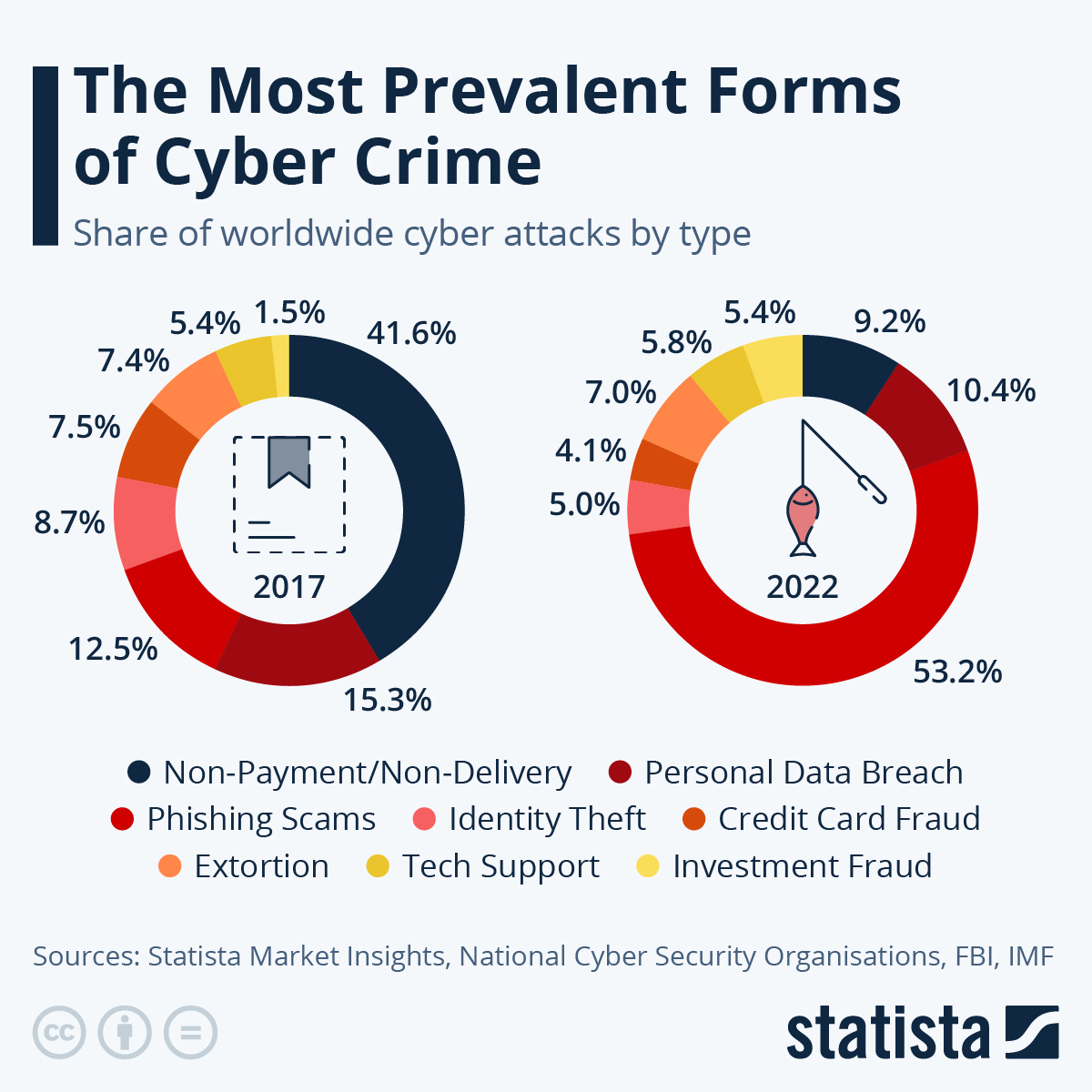
Ultimate Conclusion
Source: statcdn.com
The Ponemon Institute’s report on healthcare cybersecurity paints a stark picture, but it also offers a pathway forward. While the 88% figure is alarming, it underscores the critical need for proactive measures. By understanding the common attack vectors, strengthening security protocols, and fostering collaboration across the industry, healthcare organizations can significantly reduce their risk. The future of healthcare cybersecurity hinges on a collective commitment to innovation, vigilance, and a shared responsibility to protect patient data and ensure the integrity of the system.
Clarifying Questions: 88 Percent Healthcare Organizations Report Cyberattack Ponemon Institute
What types of data are most commonly targeted in these attacks?
Patient Protected Health Information (PHI) is the primary target, including medical records, insurance details, and personal identifying information.
How can small healthcare practices better protect themselves?
Small practices should prioritize employee training on phishing and social engineering, implement strong password policies, and consider managed security service providers (MSSPs) for cost-effective protection.
What is the role of insurance in mitigating cyberattack losses?
Cybersecurity insurance can help cover costs associated with incident response, legal fees, and ransom payments, but it’s crucial to have a robust security plan in place first.
Are there any government incentives for improving healthcare cybersecurity?
Some governments offer grants and resources to help healthcare organizations improve their cybersecurity posture; it’s advisable to check with relevant agencies for specific programs.