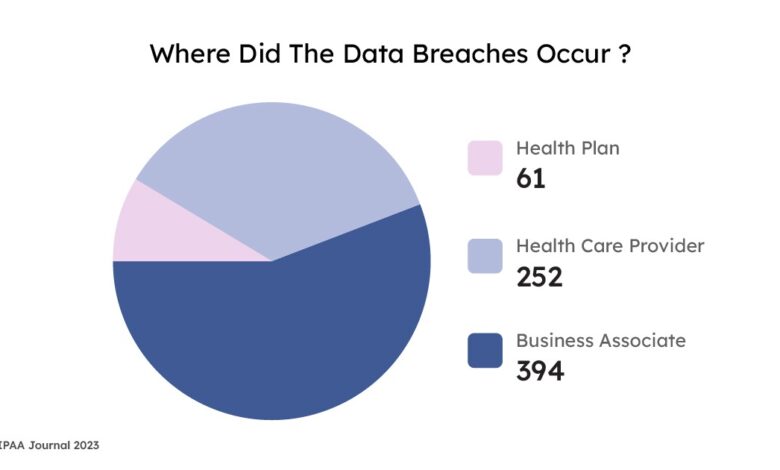
Tracking Healthcare Data Breaches Cybersecurity Hacking Hospitals
Tracking healthcare data breaches cybersecurity hacking hospitals – Tracking healthcare data breaches, cybersecurity hacking hospitals – it’s a chilling reality. We’re talking about sensitive patient information, life-saving research, and the very fabric of our healthcare system under constant threat. This isn’t just about numbers and statistics; it’s about real people, real lives, and the devastating consequences of a successful attack. This post dives into the world of healthcare cybersecurity, exploring the vulnerabilities, the threats, and the crucial steps we must take to protect our hospitals and the patients they serve.
From phishing scams to sophisticated malware, the methods used to breach healthcare systems are constantly evolving. We’ll examine the different types of attacks, the data at risk (think Protected Health Information, or PHI, financial records, and more), and the devastating financial, legal, and reputational repercussions for hospitals caught in the crosshairs. But it’s not all doom and gloom.
We’ll also discuss proactive measures, robust security protocols, and the vital role of employee training in building a more resilient healthcare ecosystem.
Types of Healthcare Data Breaches
Healthcare data breaches are a significant threat, impacting patient privacy, trust, and the overall security of the healthcare system. Understanding the different types of breaches and their associated vulnerabilities is crucial for implementing effective preventative measures. This analysis explores various breach categories, focusing on attack vectors and the specific data at risk.
Categorization of Healthcare Data Breaches by Attack Vector
Healthcare data breaches can be categorized based on the method used by attackers to gain unauthorized access. These methods often involve exploiting vulnerabilities in systems, applications, or human behavior.
| Breach Type | Description | Common Targets | Mitigation Strategies |
|---|---|---|---|
| Phishing Attacks | Malicious emails or text messages designed to trick individuals into revealing sensitive information, such as usernames, passwords, or financial data. These often impersonate legitimate organizations. For example, an email appearing to be from a hospital asking for password resets. | Employees, patients, medical staff | Security awareness training, multi-factor authentication (MFA), email filtering and anti-phishing software. |
| Malware Infections | Introduction of malicious software, such as ransomware, viruses, or Trojans, into a healthcare system. Ransomware encrypts data and demands payment for its release, while other malware might steal data or disrupt operations. An example is a ransomware attack that encrypts electronic health records (EHRs). | Servers, workstations, mobile devices | Robust antivirus and anti-malware software, regular software updates, network segmentation, data backups. |
| Insider Threats | Breaches caused by malicious or negligent actions of individuals within the organization, such as employees, contractors, or medical staff. This could involve stealing data, sabotaging systems, or unintentionally exposing information. An example is a disgruntled employee stealing patient data. | All data within the organization | Background checks, access control policies, monitoring employee activity, robust security awareness training. |
| Hacking and Network Intrusions | Direct attacks on a healthcare organization’s network infrastructure, aiming to gain unauthorized access to systems and data. This might involve exploiting vulnerabilities in network devices or using brute-force attacks to crack passwords. An example is a SQL injection attack targeting a hospital database. | Databases, servers, network devices | Firewall implementation, intrusion detection/prevention systems (IDS/IPS), regular security audits, vulnerability scanning. |
| Third-Party Vulnerabilities | Breaches resulting from security weaknesses in systems or services provided by third-party vendors. This could involve compromised cloud services or vulnerabilities in medical devices connected to the network. For example, a vulnerability in a medical imaging system allowing unauthorized access. | Data shared with third-party vendors | Careful vendor selection, thorough security assessments of third-party systems, contractual agreements outlining security responsibilities. |
Types of Compromised Data
The data compromised in healthcare breaches varies depending on the attack vector and the targeted systems. However, several common types of data are frequently targeted.Protected Health Information (PHI) is the most sensitive data compromised, including names, addresses, medical records, Social Security numbers, and insurance information. Financial data, such as credit card numbers and billing information, is also frequently targeted.
Research data, including patient data used for research purposes, can also be stolen. Intellectual property, such as proprietary software or research findings, is another potential target. The consequences of a breach can be severe, leading to financial losses, reputational damage, legal liabilities, and erosion of patient trust.
Tracking healthcare data breaches, cybersecurity hacking incidents in hospitals, is a constant uphill battle. Solutions are desperately needed, and advancements like those discussed in this article on google cloud healthcare amy waldron generative AI could offer a glimmer of hope. Perhaps AI-powered systems can help predict and prevent future breaches, strengthening our defenses against these devastating attacks on patient privacy.
Cybersecurity Threats Targeting Hospitals: Tracking Healthcare Data Breaches Cybersecurity Hacking Hospitals

Source: eusemcongress.org
Hospitals face a unique and amplified threat landscape in the realm of cybersecurity. Their reliance on complex, interconnected systems, coupled with the highly sensitive nature of patient data, makes them prime targets for malicious actors. The consequences of a successful attack can be devastating, impacting patient care, financial stability, and public trust.The interconnected nature of hospital systems presents a significant vulnerability.
From electronic health records (EHRs) and medical devices to administrative networks and billing systems, a breach in one area can quickly compromise the entire infrastructure. This intricate web of systems, often built incrementally over time with varying levels of security, creates numerous entry points for attackers. Furthermore, the constant flow of data between different departments and external entities, such as labs and insurance providers, expands the attack surface.
Prevalent Hacking Techniques Targeting Hospitals
Several hacking techniques are commonly employed against hospitals. Ransomware attacks, for example, are particularly devastating, encrypting critical data and demanding a ransom for its release. This can cripple hospital operations, delaying or preventing essential medical procedures. Phishing attacks, which exploit human error by tricking individuals into revealing sensitive information, are another frequent vector. These attacks often target employees with malicious emails or websites designed to steal credentials or install malware.
Finally, exploiting vulnerabilities in medical devices, such as insulin pumps or pacemakers, presents a direct threat to patient safety and well-being. These devices often lack robust security measures and can be remotely compromised. The impact of these attacks ranges from data breaches and financial losses to disruptions in patient care and even potential harm to patients.
Comparison of Cybersecurity Threats Across Industries
While many industries face cybersecurity threats, hospitals encounter unique challenges. The financial industry, for example, faces threats focused primarily on financial gain through theft or fraud. Retailers are concerned with the theft of customer data for identity theft or marketing purposes. Hospitals, however, face a convergence of threats: data breaches for financial gain, disruption of critical services, and the direct endangerment of patient lives.
The consequences of a successful attack on a hospital are far-reaching and potentially catastrophic, impacting not only the institution but also the health and well-being of patients. This makes hospitals a uniquely vulnerable and high-stakes target for cybercriminals. For instance, a successful ransomware attack on a hospital could lead to delayed surgeries, compromised patient care, and potentially even fatalities.
This contrasts sharply with a ransomware attack on a retail store, where the consequences are primarily financial.
Impact of Healthcare Data Breaches
Healthcare data breaches inflict significant damage far beyond the immediate loss of sensitive information. The consequences ripple through financial, legal, and reputational spheres, impacting not only hospitals but also patients and the broader healthcare system. Understanding these impacts is crucial for developing effective preventative measures and mitigating the fallout when breaches occur.
Financial Consequences of Healthcare Data Breaches
The financial burden on hospitals after a data breach is substantial. Costs include notification expenses (informing affected individuals), credit monitoring services for patients, forensic investigations to determine the breach’s extent and source, legal fees (potential lawsuits and regulatory fines), and the expense of improving cybersecurity infrastructure to prevent future breaches. The Anthem breach in 2015, for example, cost the company over $350 million in direct and indirect costs.
These costs can significantly strain hospital budgets, potentially diverting funds from patient care and other essential services. The cost of a breach is often amplified by the sensitive nature of the data involved, leading to higher legal and reputational risks. Furthermore, loss of patient trust can lead to a decline in patient volume, further impacting revenue.
Legal and Regulatory Ramifications of Healthcare Data Breaches
Hospitals face severe legal and regulatory repercussions following data breaches. Compliance with regulations like HIPAA (Health Insurance Portability and Accountability Act) in the US is paramount, and violations can result in hefty fines. The Office for Civil Rights (OCR) within the U.S. Department of Health and Human Services actively investigates and enforces HIPAA regulations. Beyond HIPAA, state-level laws and common law claims (such as negligence) can also lead to lawsuits from affected individuals.
The Premera Blue Cross breach, revealing the personal data of millions, resulted in significant legal battles and substantial fines. The legal process can be lengthy and costly, demanding considerable resources from the hospital’s legal team and potentially impacting its ability to function effectively.
Reputational Damage from Healthcare Data Breaches
A data breach severely damages a hospital’s reputation, impacting public trust and potentially driving patients to seek care elsewhere. Negative media coverage and public perception of compromised security can lead to a decline in patient admissions, impacting the hospital’s financial stability. The loss of public confidence can be difficult and expensive to regain, requiring extensive public relations efforts and a demonstrable commitment to improved security measures.
The long-term impact on reputation can be devastating, making it challenging to attract new patients, staff, and investors.
Impact on Patient Trust and Healthcare Access
Data breaches erode patient trust in healthcare providers. Patients may become hesitant to share personal information, hindering the provision of quality care and potentially delaying or preventing necessary treatment. This is particularly problematic for patients with chronic conditions requiring ongoing monitoring and data sharing. Fear of identity theft and medical fraud can also discourage patients from seeking healthcare services, exacerbating existing health disparities and impacting overall public health.
The fear of a breach can also create a barrier to utilizing telehealth services which rely on secure transmission of patient data.
Hypothetical Scenario: A Major Data Breach and its Cascading Effects
Imagine a scenario where a major hospital network suffers a ransomware attack, encrypting all patient medical records and billing data. The immediate impact includes disruption of patient care, as access to critical medical information is blocked. The hospital faces significant financial losses due to the downtime, ransomware payment demands (if paid), and subsequent investigation costs. Legally, the hospital faces HIPAA violations and potential lawsuits from affected patients.
Reputational damage is immense, with negative media coverage impacting patient trust and admissions. Patients experience anxiety over potential identity theft and compromised medical information, impacting their access to healthcare and their willingness to seek future care. The cascading effect impacts insurance providers who face increased claims related to identity theft, and pharmaceutical companies who might experience disruption in supply chain management due to billing system outages.
The entire healthcare ecosystem suffers from the disruption.
Data Tracking and Security Measures

Source: bieco.org
Protecting healthcare data requires a multi-layered approach that goes beyond simply reacting to breaches. Proactive measures, robust tracking systems, and advanced security technologies are crucial for maintaining patient confidentiality and complying with regulations like HIPAA. Effective data security is not a one-time fix but an ongoing process of assessment, improvement, and adaptation to evolving threats.Implementing robust data tracking and security measures involves a combination of technical safeguards, administrative procedures, and employee training.
This comprehensive strategy aims to minimize vulnerabilities, detect threats early, and respond effectively to incidents. A proactive approach minimizes the impact of potential breaches and fosters a culture of security within the healthcare organization.
Data Loss Prevention (DLP) Strategies
Data Loss Prevention (DLP) strategies are essential for preventing sensitive patient information from leaving the organization’s control. These strategies encompass a range of techniques, including implementing strict access controls, monitoring data movement, and using encryption to protect data both in transit and at rest. Effective DLP programs involve regular audits and employee training to ensure compliance. For example, a hospital might use DLP software to scan outgoing emails and prevent the transmission of protected health information (PHI) to unauthorized recipients.
Another example could be implementing strict protocols around removable storage devices, such as USB drives, to prevent the unauthorized copying of sensitive data.
Effective Cybersecurity Tools and Technologies
A robust cybersecurity infrastructure is vital for healthcare organizations. Several tools and technologies contribute to a strong security posture.
- Intrusion Detection and Prevention Systems (IDPS): These systems monitor network traffic for malicious activity, alerting administrators to potential threats and automatically blocking attacks.
- Endpoint Detection and Response (EDR): EDR solutions provide advanced threat detection and response capabilities on individual computers and devices, identifying and mitigating malware infections before they can spread.
- Security Information and Event Management (SIEM): SIEM systems collect and analyze security logs from various sources, providing a centralized view of security events and enabling faster incident response.
- Vulnerability Scanners: Regularly scanning systems for vulnerabilities helps identify and address security weaknesses before they can be exploited by attackers.
- Data Encryption: Encrypting data both at rest (on storage devices) and in transit (during transmission) is critical for protecting PHI from unauthorized access, even if a breach occurs. This includes using strong encryption algorithms and key management practices.
Implementing Robust Data Encryption and Access Control
Data encryption and access control mechanisms are fundamental components of a strong healthcare data security strategy. Encryption renders data unreadable without the correct decryption key, protecting it even if it’s stolen or lost. Access control mechanisms limit who can access specific data, ensuring that only authorized personnel can view or modify sensitive information. For example, a hospital might use role-based access control (RBAC) to grant different levels of access to different staff members based on their job responsibilities.
A physician might have access to a patient’s complete medical record, while a receptionist might only have access to basic contact information. Furthermore, implementing multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of authentication before gaining access to systems or data. This could involve a password, a one-time code from a mobile app, or a biometric scan.
The combination of robust encryption and granular access control significantly reduces the risk and impact of data breaches.
Regulatory Compliance and Healthcare Data
Source: itechindia.co
Navigating the complex world of healthcare data security requires a deep understanding of the regulations designed to protect patient information. Failure to comply can lead to severe consequences, impacting not only the organization’s reputation but also its financial stability. This section delves into the key regulations and the responsibilities of healthcare organizations in ensuring data security and privacy.The cornerstone of healthcare data protection in the United States is the Health Insurance Portability and Accountability Act of 1996 (HIPAA).
HIPAA establishes national standards for the electronic exchange of protected health information (PHI) and sets strict guidelines for its security and privacy. PHI includes any individually identifiable health information held or transmitted by a covered entity or its business associate. This broad definition encompasses a wide range of data, from medical records and billing information to genetic data and psychotherapy notes.
Non-compliance with HIPAA can result in significant financial penalties, ranging from several thousand dollars per violation to millions of dollars for widespread or willful negligence. Further, HIPAA violations can lead to reputational damage, loss of patient trust, and legal action.
HIPAA’s Key Provisions and Penalties for Non-Compliance
HIPAA’s regulations are multifaceted, covering areas such as privacy, security, and breach notification. The Privacy Rule Artikels how PHI can be used, disclosed, and protected. The Security Rule establishes standards for the security of electronic PHI. The Breach Notification Rule mandates timely notification to affected individuals and regulatory authorities in the event of a data breach. Penalties for non-compliance are tiered, depending on the severity and intent of the violation.
For example, a covered entity might face a civil monetary penalty for failing to implement reasonable safeguards, while a willful neglect of the rules could result in significantly higher penalties. The Office for Civil Rights (OCR) within the Department of Health and Human Services (HHS) is responsible for enforcing HIPAA.
Responsibilities of Healthcare Organizations in Ensuring Data Security and Privacy
Healthcare organizations bear the primary responsibility for protecting patient data. This responsibility extends beyond simply complying with the letter of the law; it involves establishing a comprehensive data security and privacy program that is actively monitored and improved. This includes implementing appropriate administrative, physical, and technical safeguards to protect PHI. Furthermore, organizations must provide appropriate training to their workforce on data security and privacy best practices.
Regular risk assessments are crucial to identify vulnerabilities and implement necessary mitigation strategies. Finally, healthcare organizations must have robust incident response plans in place to effectively manage and mitigate the impact of data breaches.
Steps Hospitals Can Take to Achieve and Maintain Regulatory Compliance
Implementing a robust compliance program requires a multi-pronged approach. The following steps Artikel key actions hospitals can take:
- Conduct regular risk assessments to identify vulnerabilities and potential threats.
- Develop and implement comprehensive security policies and procedures, aligned with HIPAA and other relevant regulations.
- Provide comprehensive training to all staff on HIPAA regulations, data security best practices, and their individual responsibilities.
- Implement strong access controls, including multi-factor authentication, to limit access to PHI only to authorized personnel.
- Encrypt PHI both in transit and at rest to protect it from unauthorized access.
- Regularly update and patch software and systems to address known vulnerabilities.
- Establish a robust incident response plan to effectively manage and mitigate the impact of data breaches.
- Maintain audit trails to track access to and changes in PHI.
- Conduct regular security audits and penetration testing to identify and address weaknesses in security controls.
- Implement a data loss prevention (DLP) program to prevent sensitive data from leaving the organization’s control.
Employee Training and Awareness
Healthcare data breaches are often preventable, and a significant factor in prevention is well-trained and aware staff. Employees are often the weakest link in cybersecurity, unintentionally exposing sensitive patient information through simple mistakes or falling prey to sophisticated attacks. Comprehensive training programs are crucial for mitigating this risk and fostering a culture of security within the healthcare organization.Effective employee training programs go beyond simple awareness campaigns.
They should incorporate interactive modules, realistic simulations, and regular refresher courses to ensure that employees remain vigilant and knowledgeable about evolving threats. The training must be tailored to the specific roles and responsibilities of each employee, acknowledging that a receptionist’s cybersecurity needs differ greatly from those of a network administrator.
Phishing Awareness Training
Phishing attacks remain a primary vector for data breaches in healthcare. These attacks often involve convincing emails or text messages that trick employees into revealing sensitive information, such as usernames, passwords, or personal data. Effective training emphasizes recognizing the hallmarks of phishing attempts, including suspicious email addresses, grammatical errors, urgent requests for information, and unusual links. Training should include simulated phishing emails, allowing employees to practice identifying and reporting suspicious messages in a safe environment.
For example, a training module might present various email examples, some legitimate and others clearly phishing attempts, asking trainees to identify the malicious emails and explain their reasoning. The training should also cover the importance of verifying the sender’s identity before clicking any links or downloading attachments.
Tracking healthcare data breaches is a constant battle against cybersecurity hacking in hospitals. The recent staffing shortages, highlighted by the intense negotiations during the new york state nurse strike at Montefiore and Richmond University , only exacerbate the problem. Overworked staff might be more vulnerable to phishing scams, increasing the risk of data breaches. Therefore, robust cybersecurity measures are more crucial than ever for patient safety and data protection.
Password Security Training
Strong password hygiene is paramount in preventing unauthorized access to sensitive data. Employees should be trained on creating complex, unique passwords for each account, avoiding easily guessable information such as birthdays or pet names. The training should emphasize the importance of password managers to securely store and manage multiple passwords. Regular password changes, following organizational guidelines, are also crucial.
A training module could include a section demonstrating password cracking techniques to illustrate the vulnerability of weak passwords, and then contrast this with examples of strong, complex passwords. Employees should also be educated on the dangers of password reuse across multiple platforms.
Data Handling Protocols Training
Healthcare employees handle highly sensitive patient data daily. Training should cover appropriate data handling protocols, including secure data storage, access control, and data disposal methods. This includes understanding and adhering to HIPAA regulations and other relevant privacy laws. The training should emphasize the importance of protecting patient data both electronically and physically. For instance, the training should explain the risks associated with leaving computers unattended with sensitive data displayed on the screen, or improperly disposing of documents containing patient information.
A module might include a scenario-based exercise where employees are presented with various data handling situations and asked to identify the best course of action. This interactive approach helps reinforce the importance of secure data handling practices.
Sample Training Module: Cybersecurity Concepts for Healthcare Professionals, Tracking healthcare data breaches cybersecurity hacking hospitals
This module will cover key cybersecurity concepts, including:* Understanding HIPAA and other relevant regulations: This section will Artikel the legal and ethical responsibilities of healthcare professionals in protecting patient data. It will provide a clear overview of the penalties for non-compliance.* Identifying and responding to phishing attacks: This section will teach employees how to identify and report phishing attempts. It will include practical exercises and real-world examples of phishing scams.* Creating and managing strong passwords: This section will cover best practices for password creation and management, including the use of password managers.* Secure data handling and storage: This section will explain proper protocols for handling and storing sensitive patient data, both electronically and physically.* Recognizing and reporting security incidents: This section will Artikel procedures for reporting security incidents, including data breaches and suspected security vulnerabilities.* Understanding social engineering tactics: This section will cover various social engineering techniques used by attackers, such as pretexting and baiting, and strategies to avoid falling victim to these tactics.* Mobile device security: This section will cover best practices for securing mobile devices used to access healthcare data, including password protection, data encryption, and app security.
Incident Response Planning
A robust incident response plan is the cornerstone of any healthcare organization’s cybersecurity strategy. Without a well-defined plan, a data breach can quickly escalate, resulting in significant financial losses, reputational damage, and legal repercussions. A comprehensive plan Artikels proactive measures and reactive procedures to minimize the impact of a security incident. It’s not simply a document; it’s a living, breathing framework that requires regular testing and updates to remain effective.A successful incident response plan must be detailed, tested, and regularly updated.
It should clearly define roles and responsibilities, establish communication protocols, and Artikel procedures for identifying, containing, and remediating security incidents. The plan should also address legal and regulatory requirements, public relations strategies, and post-incident analysis. The speed and effectiveness of the response directly impacts the severity of the consequences.
Incident Identification and Containment
Identifying a security incident swiftly is paramount. This involves continuous monitoring of systems and networks for suspicious activity, utilizing intrusion detection systems (IDS), security information and event management (SIEM) tools, and regular security audits. Once an incident is suspected, immediate actions are required to isolate affected systems and prevent further data compromise. This might involve disconnecting infected machines from the network, blocking malicious IP addresses, and implementing temporary access restrictions.
Tracking healthcare data breaches and cybersecurity hacking in hospitals is a constant worry, especially given the sensitive nature of patient information. The recent new york state nurse strike NYSNA Montefiore Mount Sinai highlights another vulnerability – overworked staff might inadvertently increase the risk of breaches. Ultimately, robust cybersecurity measures are crucial to protect patient data and prevent further issues.
The goal is to contain the breach and prevent its spread. For example, if a phishing email is detected, immediate steps should be taken to prevent further employees from clicking the link, and systems potentially compromised should be quarantined.
Incident Remediation and Recovery
After containing the breach, the next phase focuses on remediation and recovery. This involves thoroughly investigating the root cause of the incident, eradicating malware, restoring data from backups, and patching vulnerabilities. Remediation also includes reviewing security protocols and implementing improvements to prevent similar incidents in the future. In the case of ransomware, for instance, this might involve negotiating with attackers (if deemed appropriate and safe), restoring data from backups, and implementing multi-factor authentication to prevent future attacks.
A thorough forensic investigation is crucial to understanding the extent of the breach and to inform future security enhancements.
Post-Incident Activity
Following remediation, a thorough post-incident activity is crucial. This includes analyzing the incident to identify weaknesses in security controls, documenting lessons learned, and updating the incident response plan accordingly. This phase also involves notifying affected individuals and regulatory bodies as required by law (like HIPAA in the US). For example, a post-incident review might reveal a vulnerability in a specific application, leading to an immediate patch deployment and enhanced employee training on safe email practices.
The goal is to learn from the experience and improve the organization’s overall security posture.
Incident Response Plan Flowchart
The following describes a flowchart illustrating the steps involved in responding to a data breach. Imagine a visual representation, starting with a “Security Incident Detected” box. This branches to “Initial Assessment” (determining the nature and scope of the breach). From there, the flowchart would proceed to “Containment” (isolating affected systems), then to “Eradication” (removing malware and threats). Next, “Recovery” (restoring data and systems) would follow, leading to “Post-Incident Analysis” (reviewing the event and updating security protocols).
Finally, “Notification and Reporting” (informing affected parties and regulatory bodies) concludes the process. Each stage would have associated documentation and procedures within the overall incident response plan.
Conclusion
The fight against healthcare data breaches is an ongoing battle, demanding constant vigilance and adaptation. While the challenges are significant, the potential rewards – protecting patient lives, maintaining trust, and safeguarding the integrity of our healthcare system – are immeasurable. By understanding the threats, implementing robust security measures, and fostering a culture of cybersecurity awareness, we can significantly reduce the risk and build a more secure future for healthcare.
This isn’t just a technological issue; it’s a human one, requiring collaboration, innovation, and a shared commitment to protecting the most vulnerable among us.
Answers to Common Questions
What is the average cost of a healthcare data breach?
The cost varies widely depending on the size and scope of the breach, but it can run into millions of dollars, including legal fees, regulatory fines, and the cost of remediation.
How can patients protect themselves from healthcare data breaches?
Patients can protect themselves by being vigilant about phishing scams, using strong passwords, and reporting any suspicious activity to their healthcare provider immediately.
What is the role of insurance companies in healthcare data breaches?
Insurance companies often play a crucial role in covering the costs associated with a data breach, including legal fees, notification costs, and credit monitoring for affected patients. However, coverage can vary widely depending on the specific policy.
What are some examples of successful healthcare data breach mitigation strategies?
Successful mitigation strategies include implementing multi-factor authentication, robust data encryption, regular security audits, and comprehensive employee training programs.